Recently, DOCGuard has identified several RTF samples uploaded to our cloud. Upon further investigation, it has been determined that these samples are associated with the RoyalRoad tool.
Royal Road tool:
RoyalRoad is a highly sophisticated hacking tool that has been used by various advanced persistent threat (APT) groups to compromise targeted systems. This malware is known to exploit previously unknown vulnerabilities in the Microsoft Equation Editor service to create corrupted RTF documents that can be used to trick victims into executing the malware.
Multiple APT groups, including IceFog, Goblin Panda, Molerats, and others, have been observed using the RoyalRoad malware in various campaigns. One notable example of the RoyalRoad malware in action was its use in a high-profile attack against the Mongolian Ministry of Foreign Affairs.
Kill Chain of Royal Road
The attack chain commences with a phishing attack, in which the victim receives a malicious RTF file. Once the victim opens the RTF file, it contains a concealed encoded file that is subsequently decoded and executed using a shellcode. The executed file then executes process injection, injecting itself into a legitimate process and establishing a connection with the attacker’s Command and Control (C2) server.
Technical Analysis
According to an article from Recorded Future, the threat actor known as TA413 continues to leverage variants of the widely shared Royal Road RTF weaponizer tool in targeted phishing attempts. Chinese state-sponsored groups commonly usu this tool.
Our analysis revealed that the document in question is an RTF file that 34 different security solutions have flagged. We were able to confirm that the file exploits several known vulnerabilities, including CVE-2017-11882, CVE-2017-8759, CVE-2018-0802, and CVE-2018-0798.
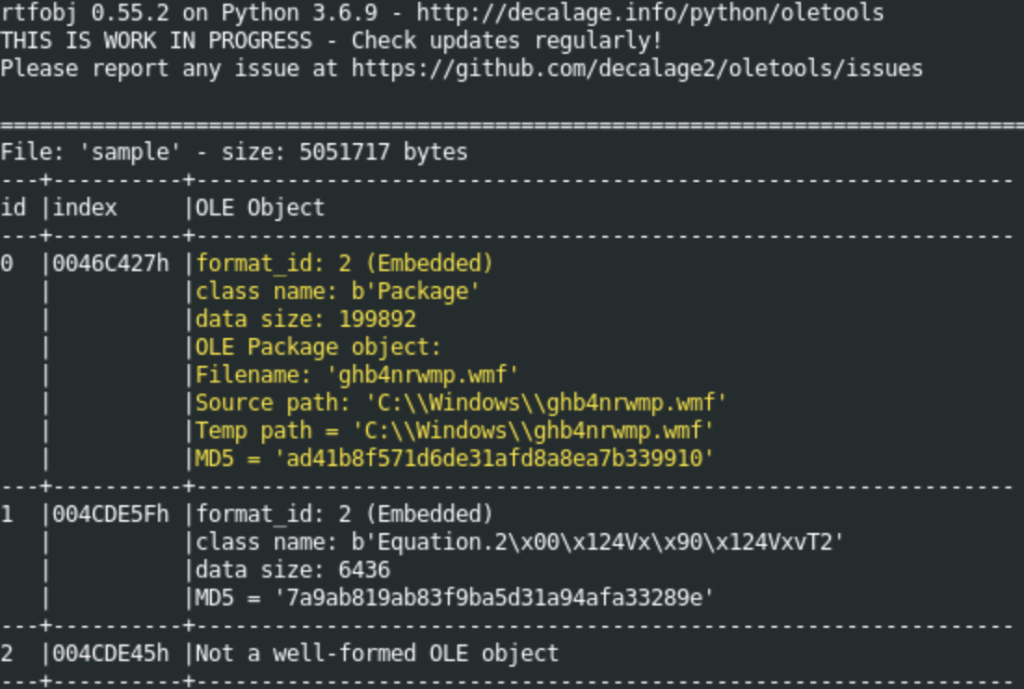
Utilizing the rtfobj tool, we successfully extracted various objects from the RTF document in question. Upon thoroughly examining these objects, we identified the presence of exploit code. This exploit code was found to drop and encode a payload in the temporary folder Temp\ghb4nrwmp.wmf.
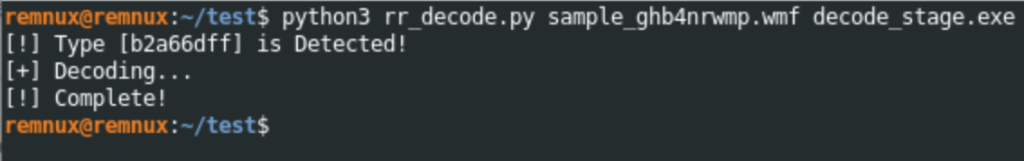
In order to properly decode the encoded payload, it is recommended to utilize the script created by the nao-sec team. Utilizing this script will allow for the successful decoding of the payload
The decoded stage of the attack vector utilizes process injection techniques to introduce the final payload onto the targeted system. This payload serves as a backdoor, allowing the attacker to exfiltrate information about the infected system to drop further modules for additional exploitation.
We identified another docx sample uploaded to our cloud that used template injection and downloaded the RTF generated by Royal Road to download the next stage. This way, we can see the document file in the next figure.
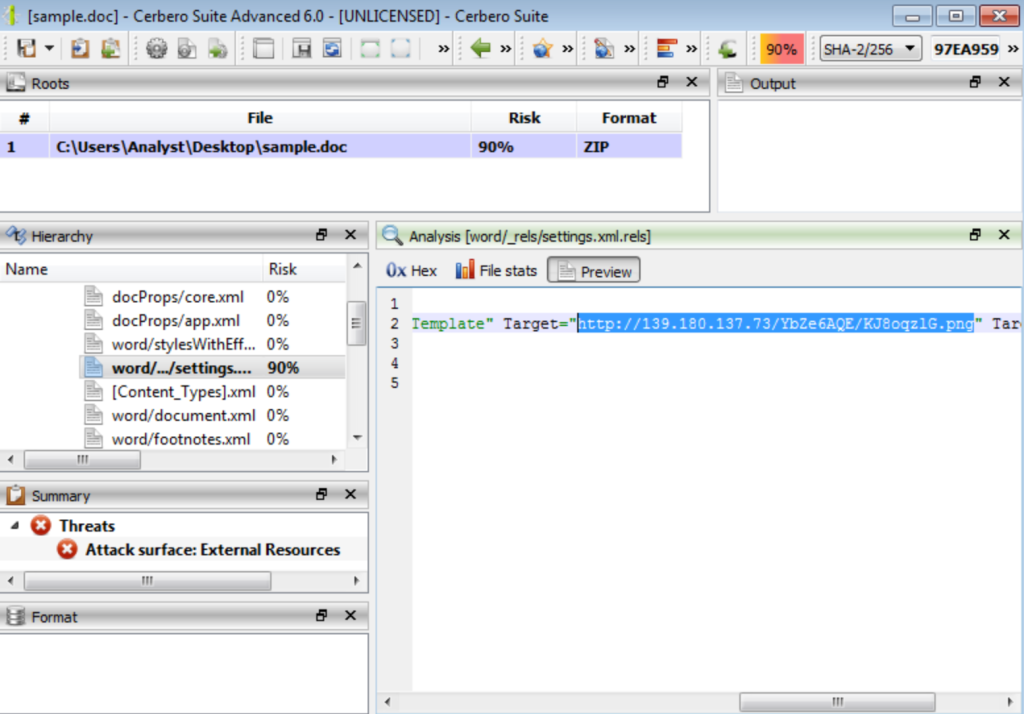
The document file utilized template injection to download the next stage across the link, as shown in the following figure.
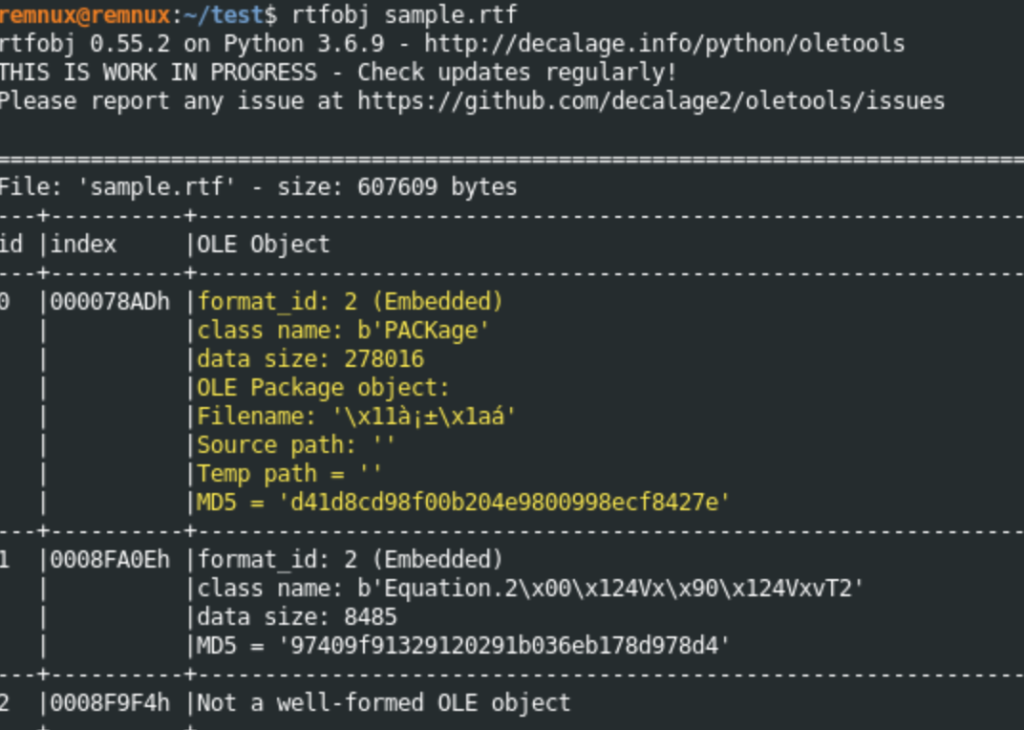
Using RTFobj, we can see that an RTF file has two objects. The first one is the encoded thread stage, and the second stage is the exploit code. This can be seen in the next figure.
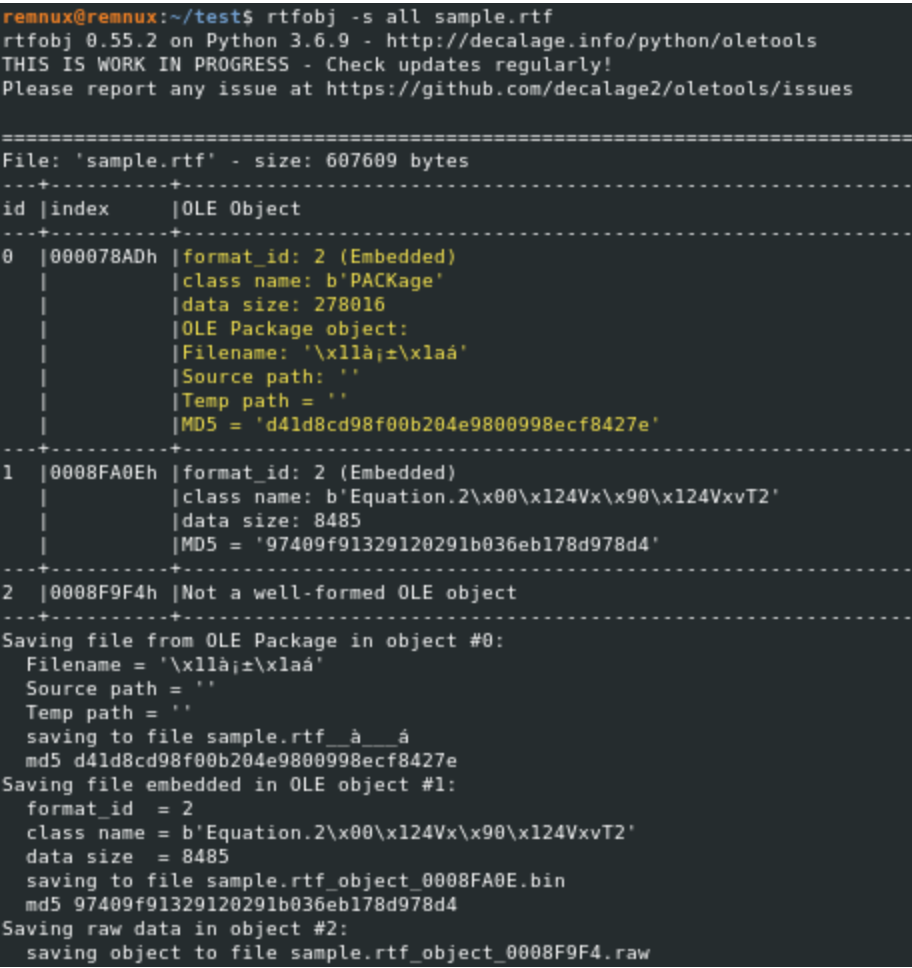
So, we can use the script created by the nao-sec team to decode the first object after dumping it, and we can see that in the next figure.
Analysis Samples With DOCGuard
First Sample
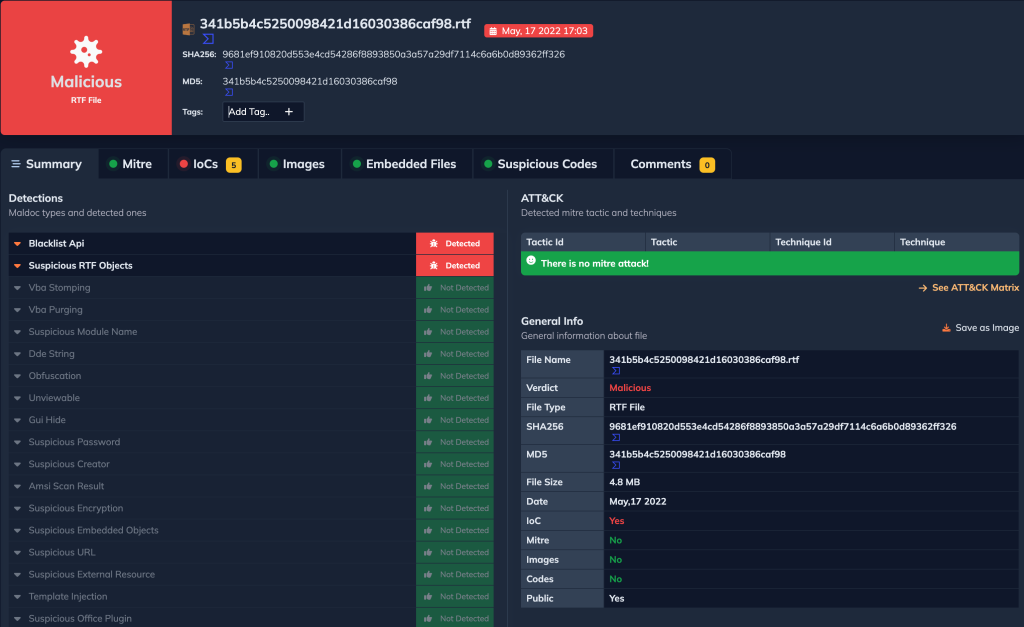
We can analyze the first sample with DOCGuard to see that the sample is marked as malicious.
- Blacklist API: The macro has some blacklisted APIs like Create and SpawnInstance Scripts, which can be embedded inside Office documents as macros that can be set to execute when files are used in Spearphishing Attachment, and other types of spearphishing are opened.
- Suspicious RTF Objects: The sample document contains an embedded RTF file.
And we can see the IOCs section in the next figure.
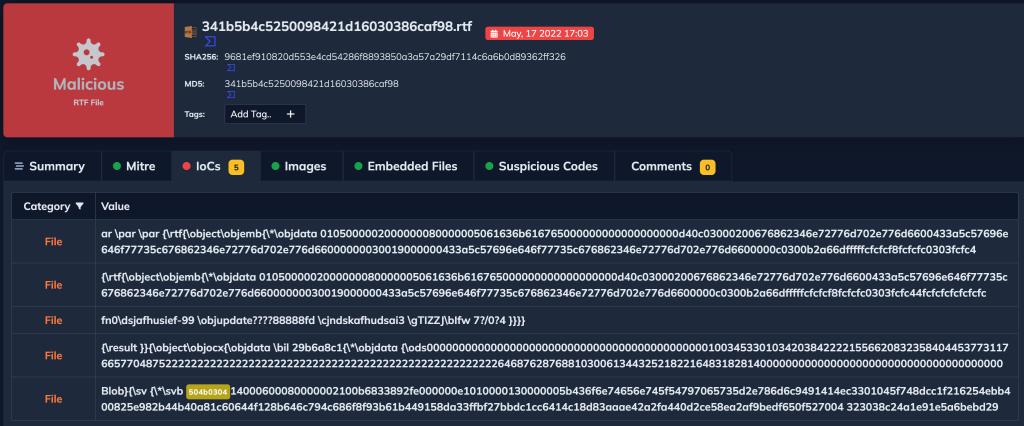
Second Sample
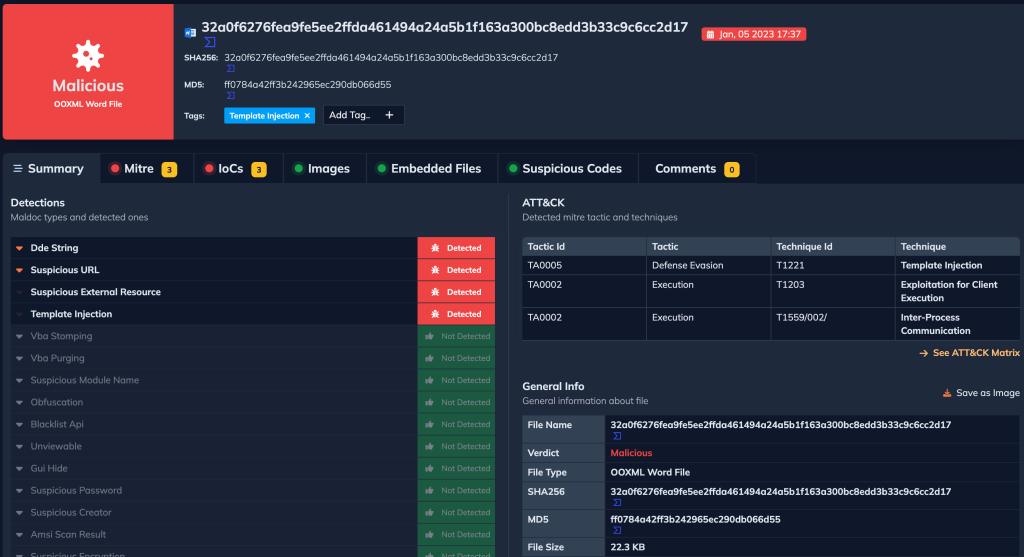
Our application marked the second sample as malicious.
- Dde String: The document is poisoned with DDE commands, directly or through embedded files Adversaries may use Windows Dynamic Data Exchange (DDE) to execute arbitrary commands.
- Suspicious URL: The sample document contains a suspicious URL.
- Suspicious External Resource
- Template Injection
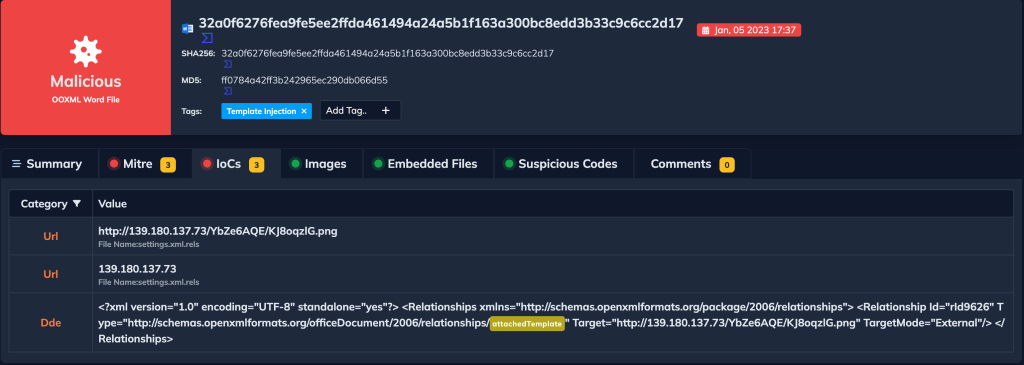
And utilized template injection to download an RTF file generated with the Royal Road tool, as shown in the following figure.
Here, we can see the IOCs section and a link that was used to download the RTF file.
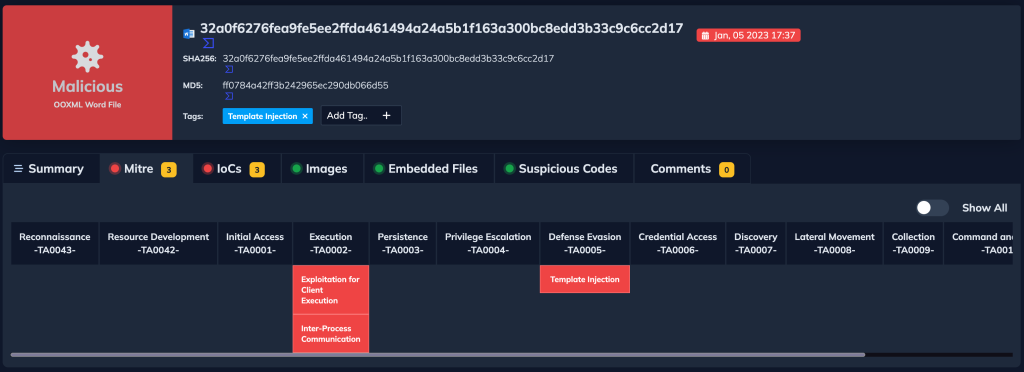
Finally, we can also check the Mittre Attack section in the following figure.
Third Sample
After downloading the third file using the link seen in the IOCs section earlier, DOCGuard detected it as malicious.
- Blacklist Api: The macro has some blacklisted APIs like Create, and SpawnInstance Scripts can be embedded inside Office documents as macros that can be set to execute when files used in Spearphishing Attachment and other types of spearphishing are opened.
- Suspicious RTF Objects: The sample document contains an embedded RTF file.
As shown in the following figure.
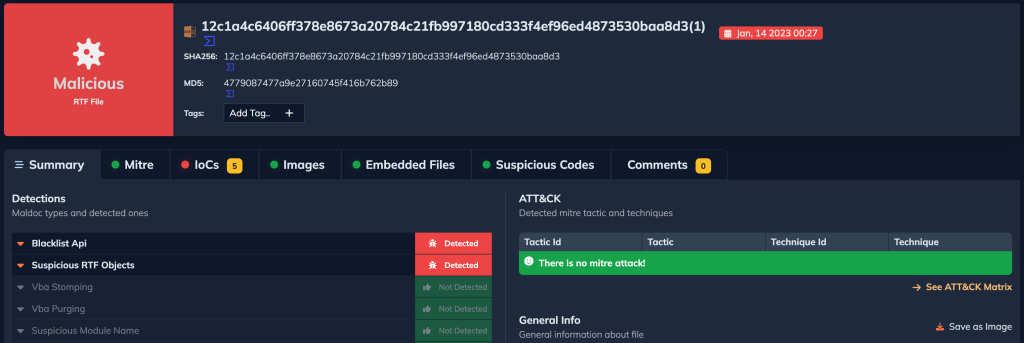
We can see the IOCs section below.
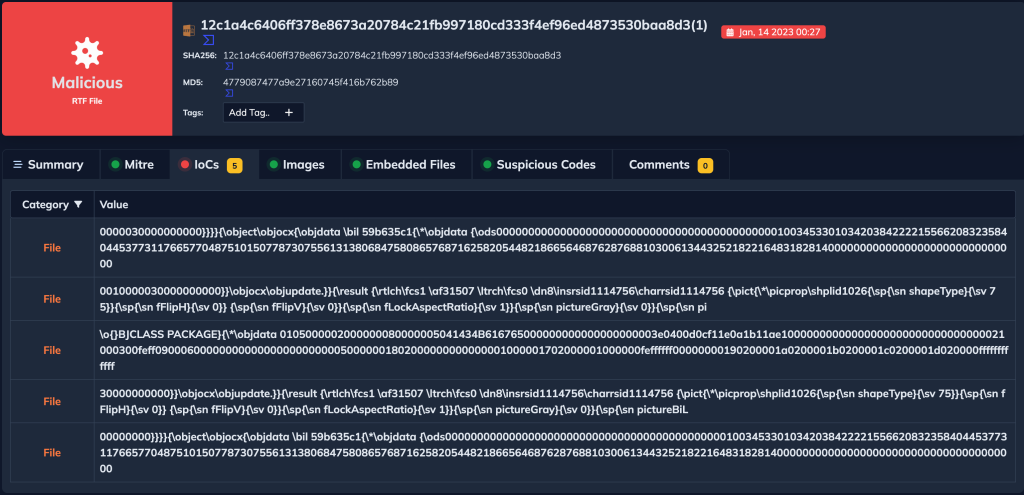
IOCs
RTFs
- 9681ef910820d553e4cd54286f8893850a3a57a29df7114c6a6b0d89362ff326
- 12c1a4c6406ff378e8673a20784c21fb997180cd333f4ef96ed4873530baa8d3
DOC
- 32a0f6276fea9fe5ee2ffda461494a24a5b1f163a300bc8edd3b33c9c6cc2d17
URL
- hxxp://139.180.137.73/YbZe6AQE/KJ8oqzlG.png
References:
- https://www.recordedfuture.com/chinese-state-sponsored-group-ta413-adopts-new-capabilities-in-pursuit-of-tibetan-targets
- https://twitter.com/nao_sec/status/1611030643693195264?s=20&t=r3MWHyUq27VTGL8y67_fkA