Attackers can create files with a PDF signature by manipulating the file structure to bypass AVs. An MHT file created in Word and containing macros is embedded in a PDF file. Then, when this file is recognized as a PDF, the embedded Word file in the PDF is opened.
When we open the malware, the Word application opens as follows.
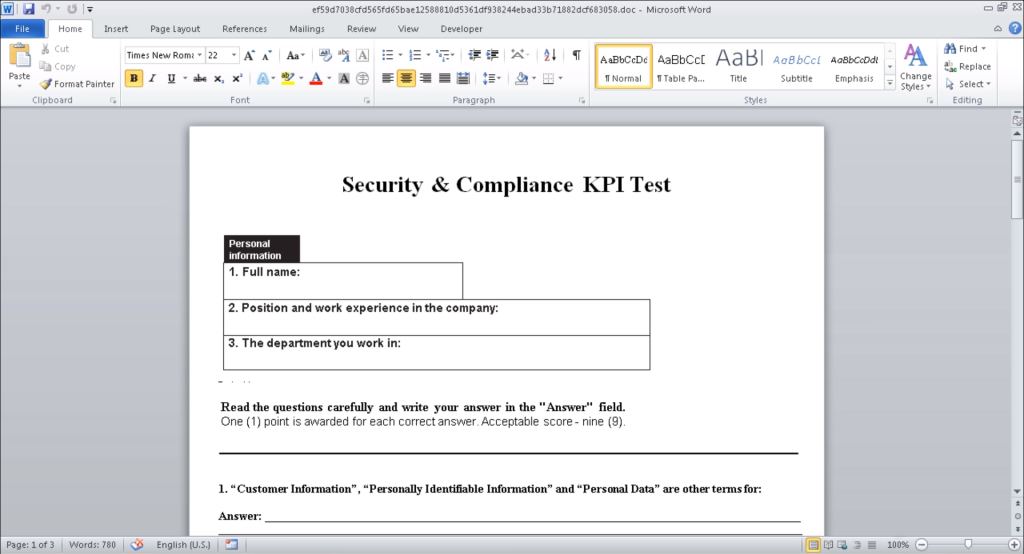
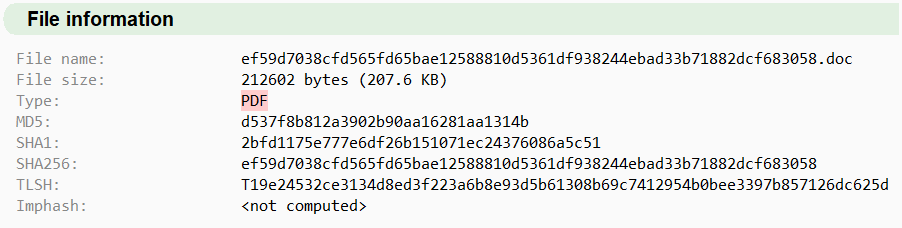
When we look at the header information of this file, we see a PDF signature.
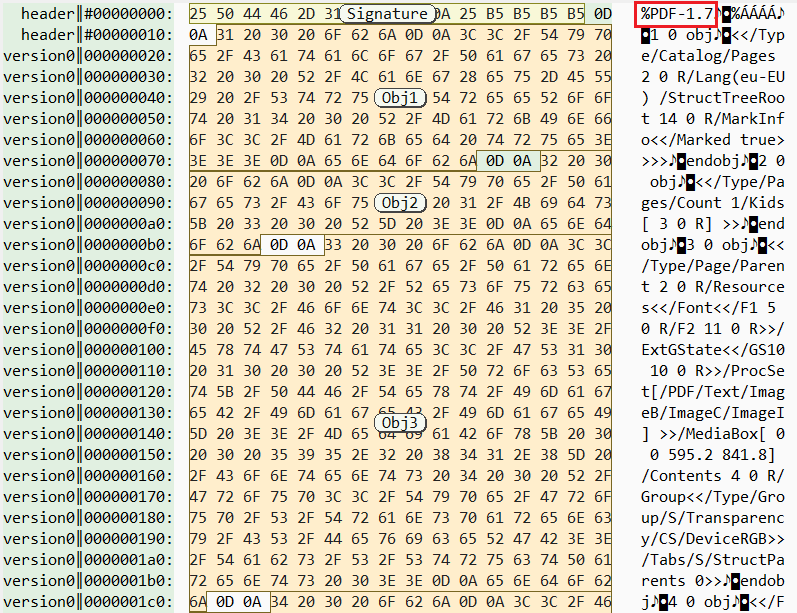
And when we open the file with the hex editor, the first bytes start with the PDF signature and then continue with other objects. It looks like a normal PDF file until here.
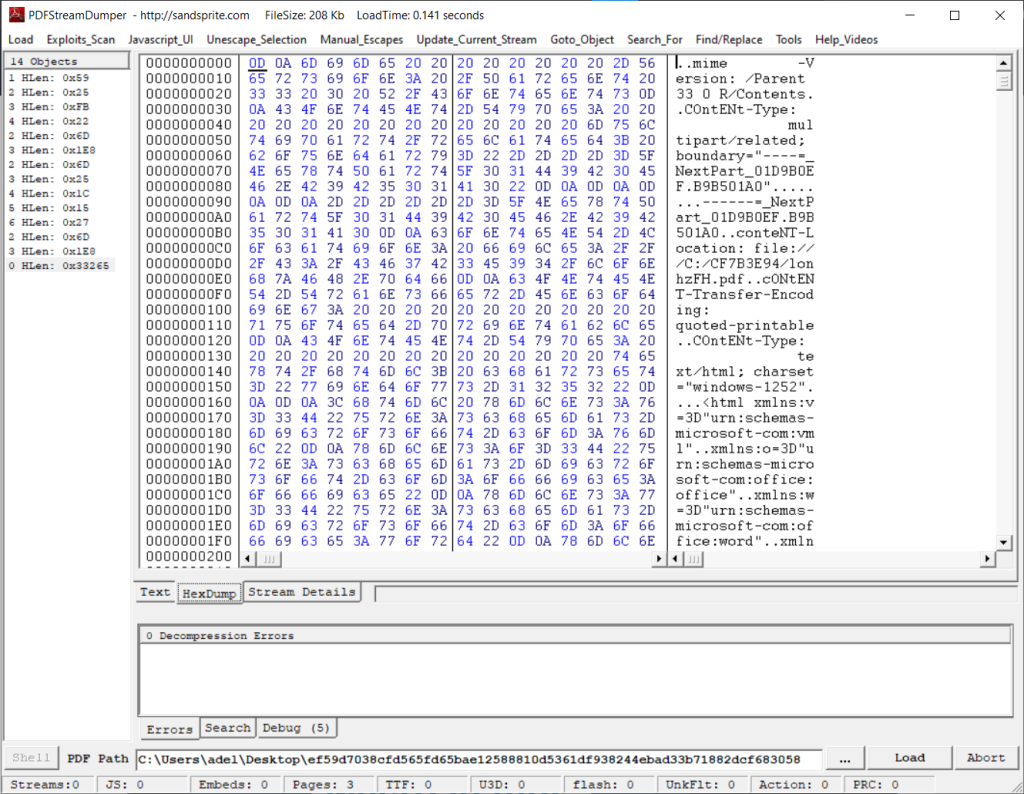
But if we analyze a little more, we can view the MHT file in other objects of the file as follows:
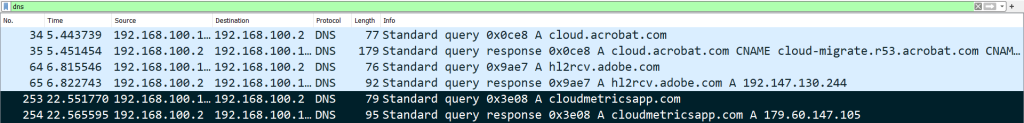
The malicious VBA codes inside the MHT start communicating with the C2 server.
Docguard Catches Every Malware!
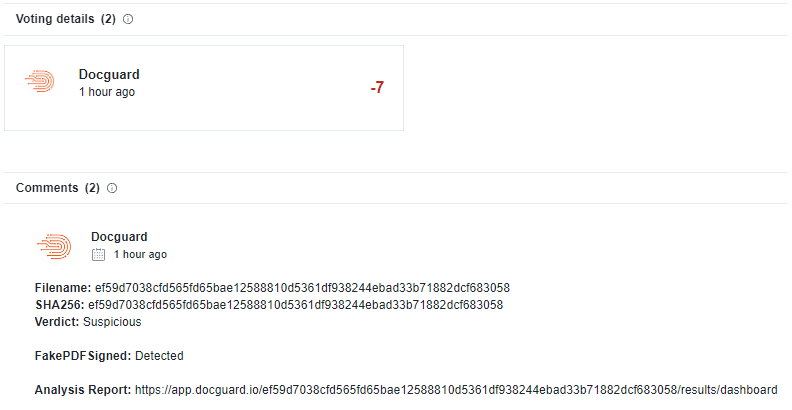
This malware bypassed all antiviruses, but DOCGuard can detect it in seconds!
IOCs
| SHA256 | 5b677d297fb862c2d223973697479ee53a91d03073b14556f421b3d74f136b9d |
| SHA256 | 098796e1b82c199ad226bff056b6310262b132f6d06930d3c254c57bdf548187 |
| SHA256 | ef59d7038cfd565fd65bae12588810d5361df938244ebad33b71882dcf683058 |
| C2 Server | https[:]//web365metrics.com |
| C2 Server | https[:]//cloudmetricsapp.com |