The analysis process of a lnk-based malware is generally based on static and AutoIt deobfuscation. To examine the important fields of the lnk file where the infection chain first starts, let’s look at its headers and commands. There is a … Read More
Real World Examples
The top AVs in the world missed all of these attacks. DOCGuard clients don’t have to worry about that.
Define the search below to see the real threats that are currently evading your Av
A Quick Analysis of Vjw0rm
Vjw0rm is a javascript-based worm. It keeps coming up with different AV bypass mechanisms day by day, and according to our research, Vjw0rm was first seen in 2020-2021. Vjw0rm can perform operations with different commands. It communicates with the C2 … Read More
Deep Dive: Analysis of Shell Link (.lnk) Files
.lnk files, commonly known as shortcuts, allow a specific application to run. Usually, users can safely access these files on their computers and run them correctly. However, malicious actors have the potential to use these files to trick users into … Read More
Phishing HTML with Zero Detection on VT and Bazaar
VT: 0/58 MB: 0/8 Filename: pl2auth.html MD5:1ce0a94c569efcaffb106b5624820030 IOCs: https[:]//sendargo[.]sbs/loqs/play/one/send[.]php https[:]//iprisky[.]sbs/mx2.2/?access= Report: Click here
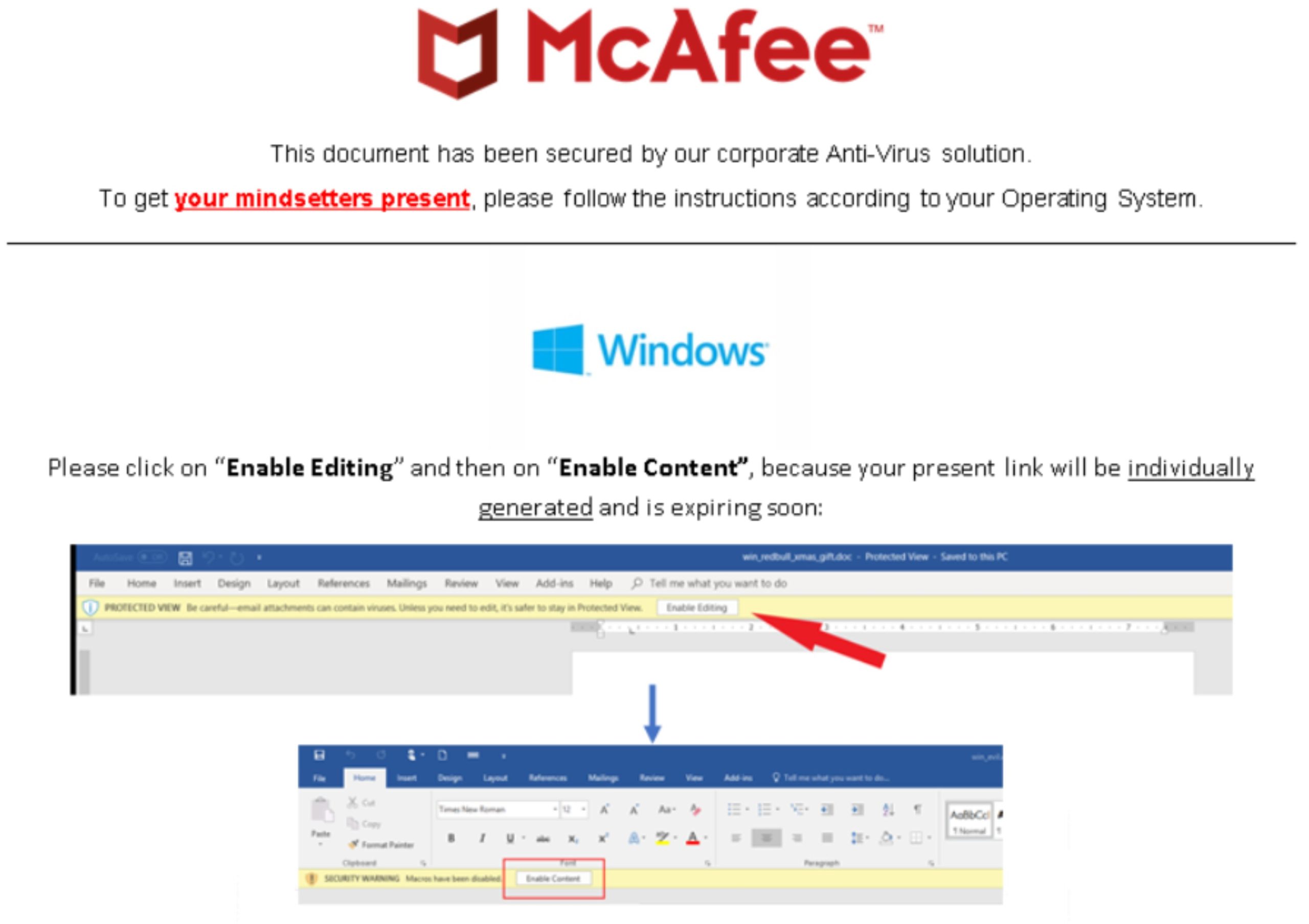
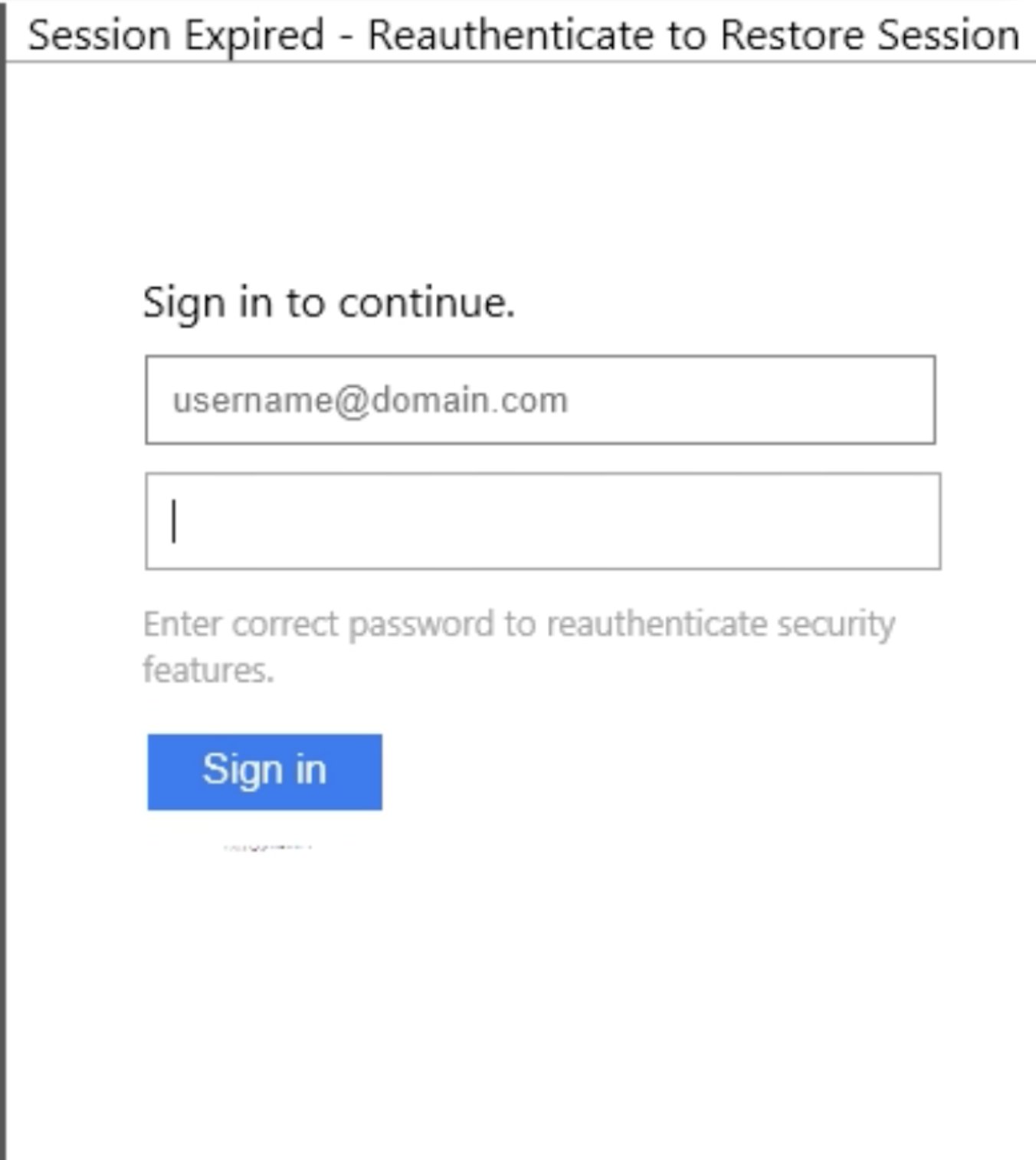
Social Engineering Test Evaded Nearly all the AVs
VT: 1/61 Filename:mindsetters_present1.doc MD5:4d5d951f2033e7e926395e8e0f7de847 IOCs: http[:]//ec2-34-255-85-35.eu-west-1.compute.amazonaws.com/api/rbuser Report: Click here